HomeAutomation
Automation
Showing 1 - 10 of 97 results
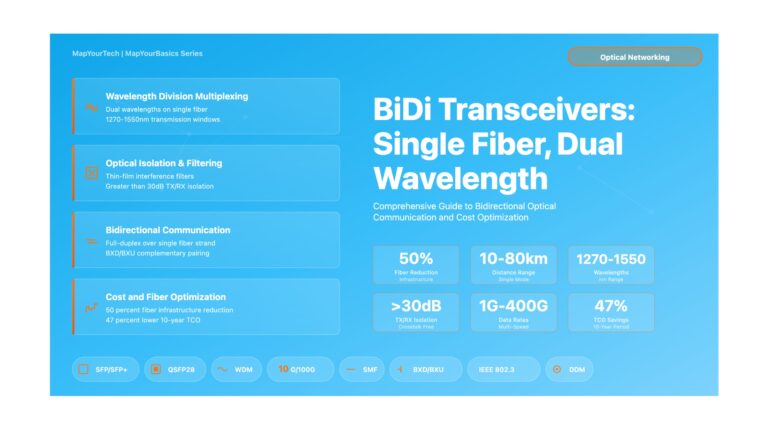
BiDi Transceivers: Single Fiber, Dual Wavelength Communication BiDi Transceivers: Single Fiber, Dual Wavelength Communication Comprehensive Guide to Bidirectional Optical Transmission...
-
Free
-
January 28, 2026
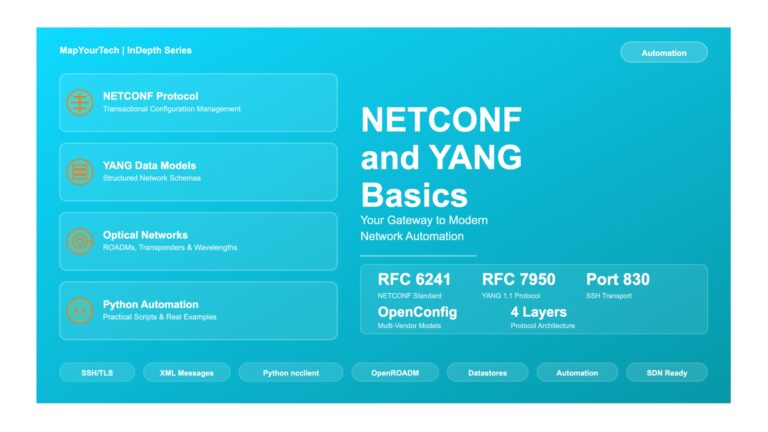
NETCONF and YANG Basics: Your Gateway to Modern Optical Network Automation NETCONF and YANG Basics: Your Gateway to Modern Optical...
-
Free
-
January 27, 2026
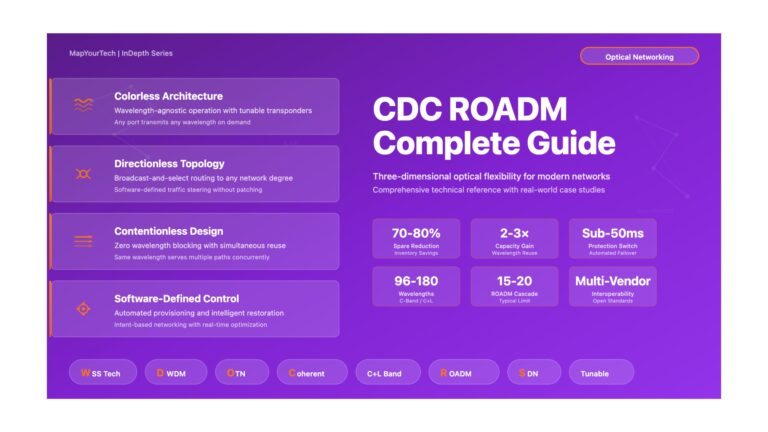
CDC ROADMs: Complete Technical Guide | MapYourTech CDC ROADMs: Colorless, Directionless, Contentionless Architecture Understanding CDC: Colorless, Directionless, and Contentionless Capabilities...
-
Free
-
December 24, 2025
Live C-OTDR: Repeater Loop Integration and Performance – IEEE Technical Article Live C-OTDR: Repeater Loop Integration and Performance Real-Time Distributed...
-
Free
-
December 21, 2025
SMART Cable Architecture: Sensors, Repeaters, and Data Links – Complete Visual Guide SMART Cable Architecture:Sensors, Repeaters, and Data Links A...
-
Free
-
December 21, 2025
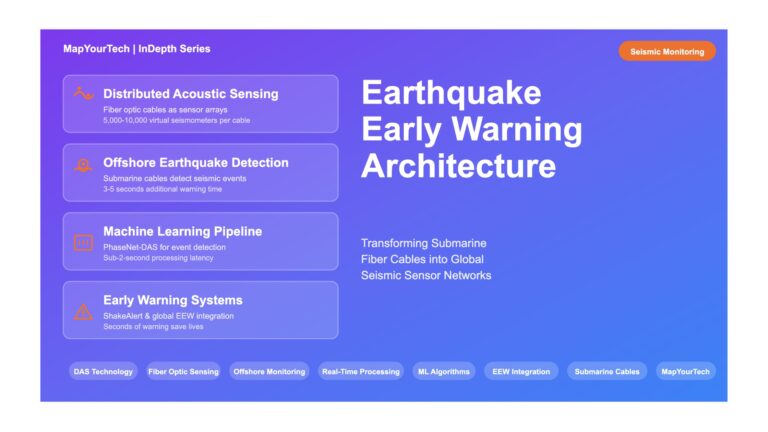
Earthquake Early Warning System Architecture: A Visual Technical Guide | MapYourTech Earthquake Early Warning System Architecture Transforming Submarine Fiber Optic...
-
Free
-
December 20, 2025
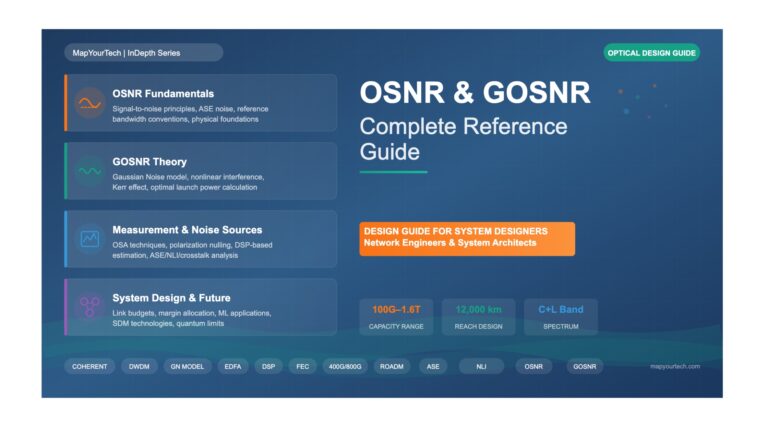
OSNR and GOSNR Complete Reference Guide – Fundamentals OSNR and GOSNR Fundamentals of Optical Signal-to-Noise Ratio 1.1 Introduction to OSNR...
-
Free
-
December 12, 2025
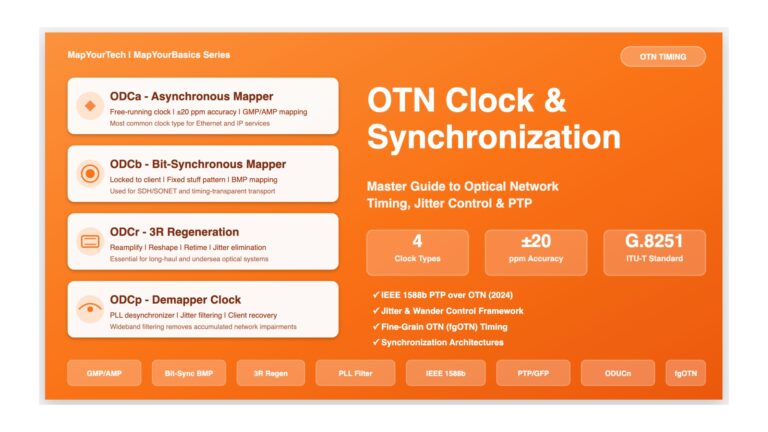
OTN Clock and Synchronization: Comprehensive Visual Guide OTN Clock and Synchronization Comprehensive Guide to Timing, Jitter Control, and Synchronization in...
-
Free
-
December 3, 2025
Access Methods for Optical Network Elements | MapYourTech Optical Network Automation Access Methods for Optical Network Elements A Comprehensive Guide...
-
Free
-
December 1, 2025
NBI and SBI Protocols at Different Layers – Part 1: Foundation & Core Concepts | MapYourTech NBI and SBI Protocols...
-
Free
-
December 1, 2025
Explore Articles
Filter Articles
ResetExplore Courses
Tags
automation
ber
Chromatic Dispersion
coherent optical transmission
Data transmission
DWDM
edfa
EDFAs
Erbium-Doped Fiber Amplifiers
fec
Fiber optics
Fiber optic technology
Forward Error Correction
Latency
modulation
network automation
network management
Network performance
noise figure
optical
optical amplifiers
optical automation
Optical communication
Optical fiber
Optical network
optical network automation
optical networking
Optical networks
Optical performance
Optical signal-to-noise ratio
Optical transport network
OSNR
OTN
Q-factor
Raman Amplifier
SDH
Signal integrity
Signal quality
Slider
submarine
submarine cable systems
submarine communication
submarine optical networking
Telecommunications
Ticker