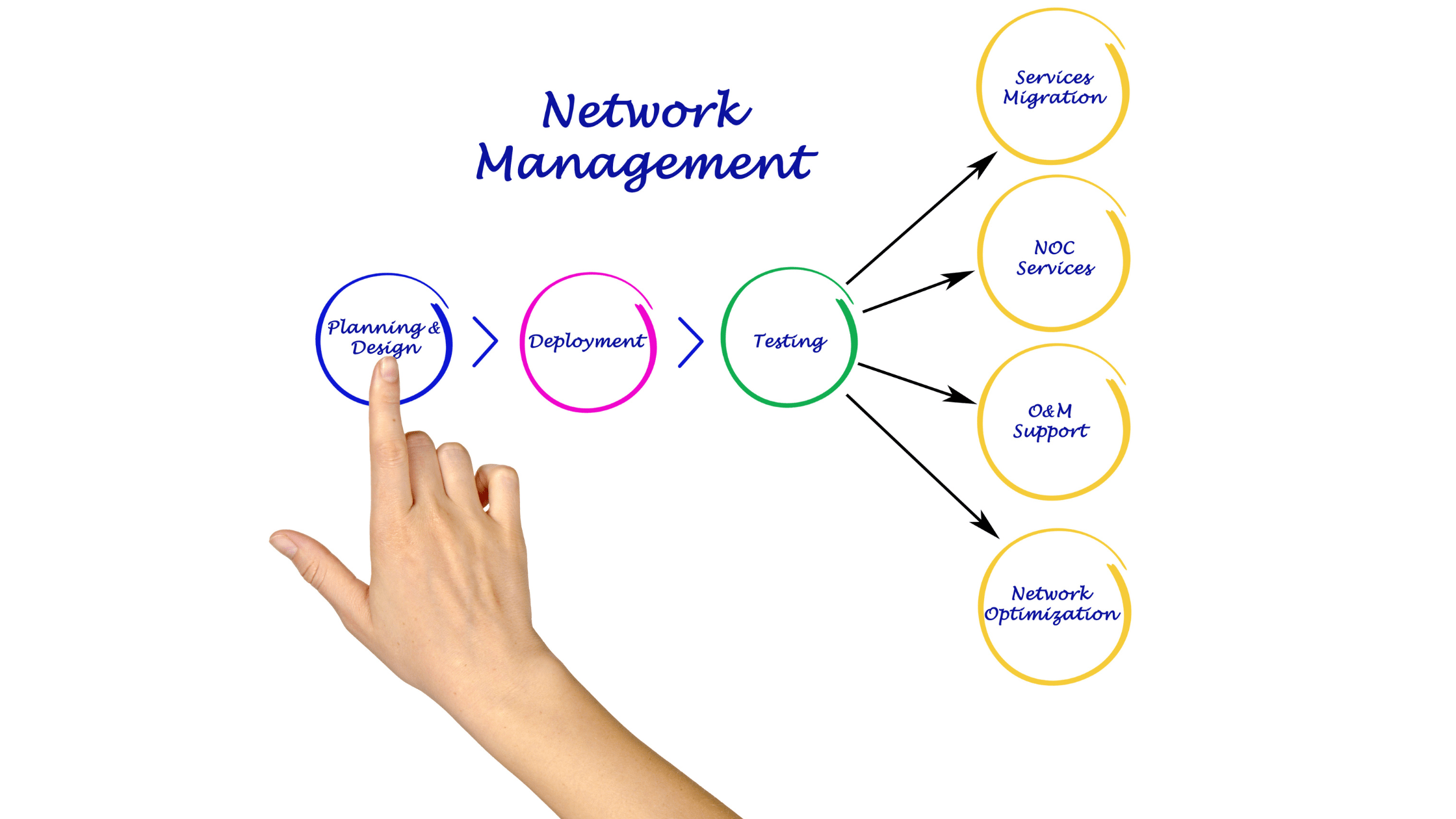
Network Management is crucial for maintaining the performance, reliability, and security of modern communication networks. With the rapid growth of network scales—from small networks with a handful of Network Elements (NEs) to complex infrastructures comprising millions of NEs—selecting the appropriate management systems and protocols becomes essential. Lets delves into the multifaceted aspects of network management, emphasizing optical networks and networking device management systems. It explores the best practices and tools suitable for varying network scales, integrates context from all layers of network management, and provides practical examples to guide network administrators in the era of automation.
1. Introduction to Network Management
Network Management encompasses a wide range of activities and processes aimed at ensuring that network infrastructure operates efficiently, reliably, and securely. It involves the administration, operation, maintenance, and provisioning of network resources. Effective network management is pivotal for minimizing downtime, optimizing performance, and ensuring compliance with service-level agreements (SLAs).
Key functions of network management include:
- Configuration Management: Setting up and maintaining network device configurations.
- Fault Management: Detecting, isolating, and resolving network issues.
- Performance Management: Monitoring and optimizing network performance.
- Security Management: Protecting the network from unauthorized access and threats.
- Accounting Management: Tracking network resource usage for billing and auditing.
In modern networks, especially optical networks, the complexity and scale demand advanced management systems and protocols to handle diverse and high-volume data efficiently.
2. Importance of Network Management in Optical Networks
Optical networks, such as Dense Wavelength Division Multiplexing (DWDM) and Optical Transport Networks (OTN), form the backbone of global communication infrastructures, providing high-capacity, long-distance data transmission. Effective network management in optical networks is critical for several reasons:
- High Throughput and Low Latency: Optical networks handle vast amounts of data with minimal delay, necessitating precise management to maintain performance.
- Fault Tolerance: Ensuring quick detection and resolution of faults to minimize downtime is vital for maintaining service reliability.
- Scalability: As demand grows, optical networks must scale efficiently, requiring robust management systems to handle increased complexity.
- Resource Optimization: Efficiently managing wavelengths, channels, and transponders to maximize network capacity and performance.
- Quality of Service (QoS): Maintaining optimal signal integrity and minimizing bit error rates (BER) through careful monitoring and adjustments.
Managing optical networks involves specialized protocols and tools tailored to handle the unique characteristics of optical transmission, such as signal power levels, wavelength allocations, and fiber optic health metrics.
3. Network Management Layers
Network management can be conceptualized through various layers, each addressing different aspects of managing and operating a network. This layered approach helps in organizing management functions systematically.
3.1. Lifecycle Management (LCM)
Lifecycle Management oversees the entire lifecycle of network devices—from procurement and installation to maintenance and decommissioning. It ensures that devices are appropriately managed throughout their operational lifespan.
- Procurement: Selecting and acquiring network devices.
- Installation: Deploying devices and integrating them into the network.
- Maintenance: Regular updates, patches, and hardware replacements.
- Decommissioning: Safely retiring old devices from the network.
Example: In an optical network, LCM ensures that new DWDM transponders are integrated seamlessly, firmware is kept up-to-date, and outdated transponders are safely removed.
3.2. Network Service Management (NSM)
Network Service Management focuses on managing the services provided by the network. It includes the provisioning, configuration, and monitoring of network services to meet user requirements.
- Service Provisioning: Allocating resources and configuring services like VLANs, MPLS, or optical channels.
- Service Assurance: Monitoring service performance and ensuring SLAs are met.
- Service Optimization: Adjusting configurations to optimize service quality and resource usage.
Example: Managing optical channels in a DWDM system to ensure that each channel operates within its designated wavelength and power parameters to maintain high data throughput.
3.3. Element Management Systems (EMS)
Element Management Systems are responsible for managing individual network elements (NEs) such as routers, switches, and optical transponders. EMS handles device-specific configurations, monitoring, and fault management.
- Device Configuration: Setting up device parameters and features.
- Monitoring: Collecting device metrics and health information.
- Fault Management: Detecting and addressing device-specific issues.
Example: An EMS for a DWDM system manages each optical transponder’s settings, monitors signal strength, and alerts operators to any deviations from normal parameters.
3.4. Business Support Systems (BSS)
Business Support Systems interface the network with business processes. They handle aspects like billing, customer relationship management (CRM), and service provisioning from a business perspective.
- Billing and Accounting: Tracking resource usage for billing purposes.
- CRM Integration: Managing customer information and service requests.
- Service Order Management: Handling service orders and provisioning.
Example: BSS integrates with network management systems to automate billing based on the optical channel usage in an OTN setup, ensuring accurate and timely invoicing.
3.5. Software-Defined Networking (SDN) Orchestrators and Controllers
SDN Orchestrators and Controllers provide centralized management and automation capabilities, decoupling the control plane from the data plane. They enable dynamic network configuration and real-time adjustments based on network conditions.
- SDN Controller: Manages the network’s control plane, making decisions about data flow and configurations.
- SDN Orchestrator: Coordinates multiple controllers and automates complex workflows across the network.
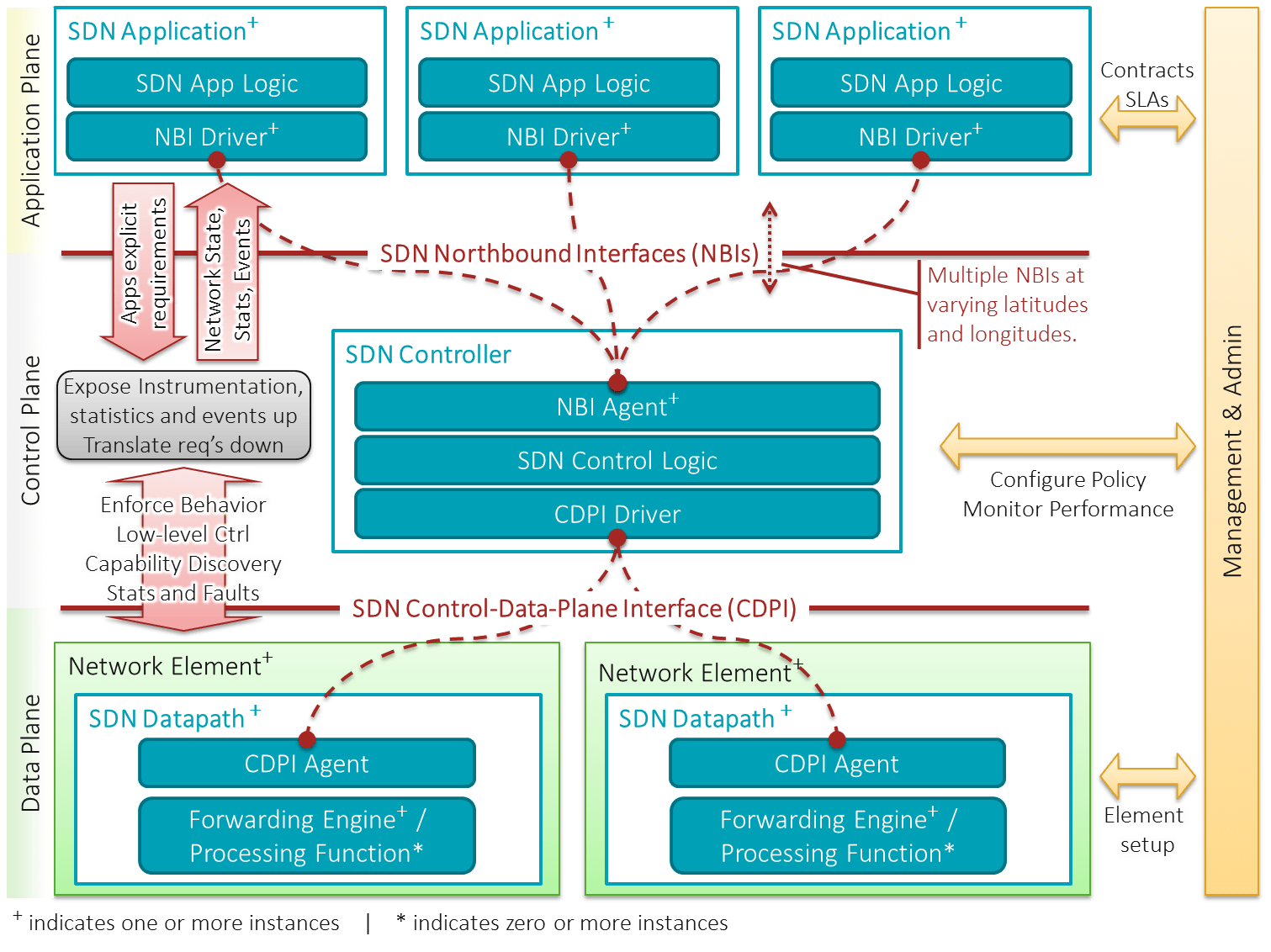
Image Credit: Wiki
Example: In an optical network, an SDN orchestrator can dynamically adjust wavelength allocations in response to real-time traffic demands, optimizing network performance and resource utilization.
4. Network Management Protocols and Standards
Effective network management relies on various protocols and standards designed to facilitate communication between management systems and network devices. This section explores key protocols, their functionalities, and relevant standards.
4.1. SNMP (Simple Network Management Protocol)
SNMP is one of the oldest and most widely used network management protocols, primarily for monitoring and managing network devices.
- Versions: SNMPv1, SNMPv2c, SNMPv3
- Standards:
- RFC 1157: SNMPv1
- RFC 1905: SNMPv2
- RFC 3411-3418: SNMPv3
Key Features:
- Monitoring: Collection of device metrics (e.g., CPU usage, interface status).
- Configuration: Basic configuration through SNMP SET operations.
- Trap Messages: Devices can send unsolicited alerts (traps) to managers.
Advantages:
- Simplicity: Easy to implement and use for basic monitoring.
- Wide Adoption: Supported by virtually all network devices.
- Low Overhead: Lightweight protocol suitable for simple tasks.
Disadvantages:
- Security: SNMPv1 and SNMPv2c lack robust security features. SNMPv3 addresses this but is more complex.
- Limited Functionality: Primarily designed for monitoring, with limited configuration capabilities.
- Scalability Issues: Polling large numbers of devices can generate significant network traffic.
Use Cases:
- Small to medium-sized networks for basic monitoring and alerting.
- Legacy systems where advanced management protocols are not supported.
4.2. NETCONF (Network Configuration Protocol)
NETCONF is a modern network management protocol designed to provide a standardized way to configure and manage network devices.
- Version: NETCONF v1.1
- Standards:
- RFC 6241: NETCONF Protocol
- RFC 6242: NETCONF over TLS
Key Features:
- Structured Configuration: Uses XML/YANG data models for precise configuration.
- Transactional Operations: Supports atomic commits and rollbacks to ensure configuration integrity.
- Extensibility: Modular and extensible, allowing for customization and new feature integration.
Advantages:
- Granular Control: Detailed configuration capabilities through YANG models.
- Transaction Support: Ensures consistent configuration changes with commit and rollback features.
- Secure: Typically operates over SSH or TLS, providing strong security.
Disadvantages:
- Complexity: Requires understanding of YANG data models and XML.
- Resource Intensive: Can be more demanding in terms of processing and bandwidth compared to SNMP.
Use Cases:
- Medium to large-sized networks requiring precise configuration and management.
- Environments where transactional integrity and security are paramount.
4.3. RESTCONF
RESTCONF is a RESTful API-based protocol that builds upon NETCONF principles, providing a simpler and more accessible interface for network management.
- Version: RESTCONF v1.0
- Standards:
- RFC 8040: RESTCONF Protocol
Key Features:
- RESTful Architecture: Utilizes standard HTTP methods (GET, POST, PUT, DELETE) for network management.
- Data Formats: Supports JSON and XML, making it compatible with modern web applications.
- YANG Integration: Uses YANG data models for defining network configurations and states.
Advantages:
- Ease of Use: Familiar RESTful API design makes it easier for developers to integrate with web-based tools.
- Flexibility: Can be easily integrated with various automation and orchestration platforms.
- Lightweight: Less overhead compared to NETCONF’s XML-based communication.
Disadvantages:
- Limited Transaction Support: Does not inherently support transactional operations like NETCONF.
- Security Complexity: While secure over HTTPS, integrating with OAuth or other authentication mechanisms can add complexity.
Use Cases:
- Environments where integration with web-based applications and automation tools is required.
- Networks that benefit from RESTful interfaces for easier programmability and accessibility.
4.4. gNMI (gRPC Network Management Interface)
gNMI is a high-performance network management protocol designed for real-time telemetry and configuration management, particularly suitable for large-scale and dynamic networks.
- Version: gNMI v0.7.x
- Standards: OpenConfig standard for gNMI
Key Features:
- Streaming Telemetry: Supports real-time, continuous data streaming from devices to management systems.
- gRPC-Based: Utilizes the efficient gRPC framework over HTTP/2 for low-latency communication.
- YANG Integration: Leverages YANG data models for consistent configuration and telemetry data.
Advantages:
- Real-Time Monitoring: Enables high-frequency, real-time data collection for performance monitoring and fault detection.
- Efficiency: Optimized for high throughput and low latency, making it ideal for large-scale networks.
- Automation-Friendly: Easily integrates with modern automation frameworks and tools.
Disadvantages:
- Complexity: Requires familiarity with gRPC, YANG, and modern networking concepts.
- Infrastructure Requirements: Requires scalable telemetry collectors and robust backend systems to handle high-volume data streams.
Use Cases:
- Large-scale networks requiring real-time performance monitoring and dynamic configuration.
- Environments that leverage software-defined networking (SDN) and network automation.
4.5. TL1 (Transaction Language 1)
TL1 is a legacy network management protocol widely used in telecom networks, particularly for managing optical network elements.
- Standards:
- Telcordia GR-833-CORE
- ITU-T G.773
- Versions: Varies by vendor/implementation
Key Features:
- Command-Based Interface: Uses structured text commands for managing network devices.
- Manual and Scripted Management: Supports both interactive command input and automated scripting.
- Vendor-Specific Extensions: Often includes proprietary commands tailored to specific device functionalities.
Advantages:
- Simplicity: Easy to learn and use for operators familiar with CLI-based management.
- Wide Adoption in Telecom: Supported by many legacy optical and telecom devices.
- Granular Control: Allows detailed configuration and monitoring of individual network elements.
Disadvantages:
- Limited Automation: Lacks the advanced automation capabilities of modern protocols.
- Proprietary Nature: Vendor-specific commands can lead to compatibility issues across different devices.
- No Real-Time Telemetry: Designed primarily for manual or scripted command entry without native support for continuous data streaming.
Use Cases:
- Legacy telecom and optical networks where TL1 is the standard management protocol.
- Environments requiring detailed, device-specific configurations that are not available through modern protocols.
4.6. CLI (Command Line Interface)
CLI is a fundamental method for managing network devices, providing direct access to device configurations and status through text-based commands.
- Standards: Vendor-specific, no universal standard.
- Versions: Varies by vendor (e.g., Cisco IOS, Juniper Junos, Huawei VRP)
Key Features:
- Text-Based Commands: Allows direct manipulation of device configurations through structured commands.
- Interactive and Scripted Use: Can be used interactively or automated using scripts.
- Universal Availability: Present on virtually all network devices, including routers, switches, and optical equipment.
Advantages:
- Flexibility: Offers detailed and granular control over device configurations.
- Speed: Allows quick execution of commands, especially for power users familiar with the syntax.
- Universality: Supported across all major networking vendors, ensuring broad applicability.
Disadvantages:
- Steep Learning Curve: Requires familiarity with specific command syntax and vendor-specific nuances.
- Error-Prone: Manual command entry increases the risk of human errors, which can lead to misconfigurations.
- Limited Scalability: Managing large numbers of devices through CLI can be time-consuming and inefficient compared to automated protocols.
Use Cases:
- Manual configuration and troubleshooting of network devices.
- Environments where precise, low-level device management is required.
- Small to medium-sized networks where automation is limited or not essential.
4.7. OpenConfig
OpenConfig is an open-source, vendor-neutral initiative designed to standardize network device configurations and telemetry data across different vendors.
- Standards: OpenConfig models are community-driven and continuously evolving.
- Versions: Continuously updated YANG-based models.
Key Features:
- Vendor Neutrality: Standardizes configurations and telemetry across multi-vendor environments.
- YANG-Based Models: Uses standardized YANG models for consistent data structures.
- Supports Modern Protocols: Integrates seamlessly with NETCONF, RESTCONF, and gNMI for configuration and telemetry.
Advantages:
- Interoperability: Facilitates unified management across diverse network devices from different vendors.
- Scalability: Designed to handle large-scale networks with automated management capabilities.
- Extensibility: Modular and adaptable to evolving network technologies and requirements.
Disadvantages:
- Adoption Rate: Not all vendors fully support OpenConfig models, limiting its applicability in mixed environments.
- Complexity: Requires understanding of YANG and modern network management protocols.
- Continuous Evolution: As an open-source initiative, models are frequently updated, necessitating ongoing adaptation.
Use Cases:
- Multi-vendor network environments seeking standardized management practices.
- Large-scale, automated networks leveraging modern protocols like gNMI and NETCONF.
- Organizations aiming to future-proof their network management strategies with adaptable and extensible models.
4.8. Syslog
Syslog is a standard for message logging, widely used for monitoring and troubleshooting network devices by capturing event messages.
- Version: Defined by RFC 5424
- Standards:
- RFC 3164: Original Syslog Protocol
- RFC 5424: Syslog Protocol (Enhanced)
Key Features:
- Event Logging: Captures and sends log messages from network devices to a centralized Syslog server.
- Severity Levels: Categorizes logs based on severity, from informational messages to critical alerts.
- Facility Codes: Identifies the source or type of the log message (e.g., kernel, user-level, security).
Advantages:
- Simplicity: Easy to implement and supported by virtually all network devices.
- Centralized Logging: Facilitates the aggregation and analysis of logs from multiple devices in one location.
- Real-Time Alerts: Enables immediate notification of critical events and issues.
Disadvantages:
- Unstructured Data: Traditional Syslog messages can be unstructured and vary by vendor, complicating log analysis.
- Reliability: UDP-based Syslog can result in message loss; however, TCP-based or Syslog over TLS solutions mitigate this issue.
- Scalability: Handling large volumes of log data requires robust Syslog servers and storage solutions.
Use Cases:
- Centralized monitoring and logging of network and optical devices.
- Real-time alerting and notification systems for network faults and security incidents.
- Compliance auditing and forensic analysis through aggregated log data.
5. Network Management Systems (NMS) and Tools
Network Management Systems (NMS) are comprehensive platforms that integrate various network management protocols and tools to provide centralized control, monitoring, and configuration capabilities. The choice of NMS depends on the scale of the network, specific requirements, and the level of automation desired.
5.1. For Small Networks (10 NEs)
Best Tools:
- PRTG Network Monitor: User-friendly, supports SNMP, Syslog, and other protocols. Ideal for small networks with basic monitoring needs.
- Nagios Core: Open-source, highly customizable, supports SNMP and Syslog. Suitable for administrators comfortable with configuring open-source tools.
- SolarWinds Network Performance Monitor (NPM): Provides a simple setup with powerful monitoring capabilities. Ideal for small to medium networks.
- Element Management System from any optical/networking vendor.
Features:
- Basic monitoring of device status, interface metrics, and uptime.
- Simple alerting mechanisms for critical events.
- Easy configuration with minimal setup complexity.
Example:
A small office network with a few routers, switches, and an optical transponder can use PRTG to monitor interface statuses, CPU usage, and power levels of optical devices via SNMP and Syslog.
5.2. For Medium Networks (100 NEs)
Best Tools:
- SolarWinds NPM: Scales well with medium-sized networks, offering advanced monitoring, alerting, and reporting features.
- Zabbix: Open-source, highly scalable, supports SNMP, NETCONF, RESTCONF, and gNMI. Suitable for environments requiring robust customization.
- Cisco Prime Infrastructure: Integrates seamlessly with Cisco devices, providing comprehensive management for medium-sized networks.
- Element Management System from any optical/networking vendor.
Features:
- Advanced monitoring with support for multiple protocols (SNMP, NETCONF).
- Enhanced alerting and notification systems.
- Configuration management and change tracking capabilities.
Example:
A medium-sized enterprise with multiple DWDM systems, routers, and switches can use Zabbix to monitor real-time performance metrics, configure devices via NETCONF, and receive alerts through Syslog messages.
5.3. For Large Networks (1,000 NEs)
Best Tools:
- Cisco DNA Center: Comprehensive management platform for large Cisco-based networks, offering automation, assurance, and advanced analytics.
- Juniper Junos Space: Scalable EMS for managing large Juniper networks, supporting automation and real-time monitoring.
- OpenNMS: Open-source, highly scalable, supports SNMP, RESTCONF, and gNMI. Suitable for diverse network environments.
- Network Management System from any optical/networking vendor.
Features:
- Centralized management with support for multiple protocols.
- High scalability and performance monitoring.
- Advanced automation and orchestration capabilities.
- Integration with SDN controllers and orchestration tools.
Example:
A large telecom provider managing thousands of optical transponders, DWDM channels, and networking devices can use Cisco DNA Center to automate configuration deployments, monitor network health in real-time, and optimize resource utilization through integrated SDN features.
5.4. For Enterprise and Massive Networks (500,000 to 1 Million NEs)
Best Tools:
- Ribbon LightSoft :Comprehensive network management solution for large-scale optical and IP networks.
- Nokia Network Services Platform (NSP): Highly scalable platform designed for massive network deployments, supporting multi-vendor environments.
- Huawei iManager U2000: Comprehensive network management solution for large-scale optical and IP networks.
- Splunk Enterprise: Advanced log management and analytics platform, suitable for handling vast amounts of Syslog data.
- Elastic Stack (ELK): Open-source solution for log aggregation, visualization, and analysis, ideal for massive log data volumes.
Features:
- Extreme scalability to handle millions of NEs.
- Advanced data analytics and machine learning for predictive maintenance and anomaly detection.
- Comprehensive automation and orchestration to manage complex network configurations.
- High-availability and disaster recovery capabilities.
Example:
A global internet service provider with a network spanning multiple continents, comprising millions of NEs including optical transponders, routers, switches, and data centers, can use Nokia NSP integrated with Splunk for real-time monitoring, automated configuration management through OpenConfig and gNMI, and advanced analytics to predict and prevent network failures.
6. Automation in Network Management
Automation in network management refers to the use of software tools and scripts to perform repetitive tasks, configure devices, monitor network performance, and respond to network events without manual intervention. Automation enhances efficiency, reduces errors, and allows network administrators to focus on more strategic activities.
6.1. Benefits of Automation
- Efficiency: Automates routine tasks, saving time and reducing manual workload.
- Consistency: Ensures uniform configuration and management across all network devices, minimizing discrepancies.
- Speed: Accelerates deployment of configurations and updates, enabling rapid scaling.
- Error Reduction: Minimizes human errors associated with manual configurations and monitoring.
- Scalability: Facilitates management of large-scale networks by handling complex tasks programmatically.
- Real-Time Responsiveness: Enables real-time monitoring and automated responses to network events and anomalies.
6.2. Automation Tools and Frameworks
- Ansible: Open-source automation tool that uses playbooks (YAML scripts) for automating device configurations and management tasks.
- Terraform: Infrastructure as Code (IaC) tool that automates the provisioning and management of network infrastructure.
- Python Scripts: Custom scripts leveraging libraries like Netmiko, Paramiko, and ncclient for automating CLI and NETCONF-based tasks.
- Cisco DNA Center Automation: Provides built-in automation capabilities for Cisco networks, including zero-touch provisioning and policy-based management.
- Juniper Automation: Junos Space Automation provides tools for automating complex network tasks in Juniper environments.
- Ribbon Muse SDN orchestrator ,Cisco MDSO and Ciena MCP/BluePlanet from any optical/networking vendor.
Example:
Using Ansible to automate the configuration of multiple DWDM transponders across different vendors by leveraging OpenConfig YANG models and NETCONF protocols ensures consistent and error-free deployments.
7. Best Practices for Network Management
Implementing effective network management requires adherence to best practices that ensure the network operates smoothly, efficiently, and securely.
7.1. Standardize Management Protocols
- Use Unified Protocols: Standardize on protocols like NETCONF, RESTCONF, and OpenConfig for configuration and management to ensure interoperability across multi-vendor environments.
- Adopt Secure Protocols: Always use secure transport protocols (SSH, TLS) to protect management communications.
7.2. Implement Centralized Management Systems
- Centralized Control: Use centralized NMS platforms to manage and monitor all network elements from a single interface.
- Data Aggregation: Aggregate logs and telemetry data in centralized repositories for comprehensive analysis and reporting.
7.3. Automate Routine Tasks
- Configuration Automation: Automate device configurations using scripts or automation tools to ensure consistency and reduce manual errors.
- Automated Monitoring and Alerts: Set up automated monitoring and alerting systems to detect and respond to network issues in real-time.
7.4. Maintain Accurate Documentation
- Configuration Records: Keep detailed records of all device configurations and changes for troubleshooting and auditing purposes.
- Network Diagrams: Maintain up-to-date network topology diagrams to visualize device relationships and connectivity.
7.5. Regularly Update and Patch Devices
- Firmware Updates: Regularly update device firmware to patch vulnerabilities and improve performance.
- Configuration Backups: Schedule regular backups of device configurations to ensure quick recovery in case of failures.
7.6. Implement Role-Based Access Control (RBAC)
- Access Management: Define roles and permissions to restrict access to network management systems based on job responsibilities.
- Audit Trails: Maintain logs of all management actions for security auditing and compliance.
7.7. Leverage Advanced Analytics and Machine Learning
- Predictive Maintenance: Use analytics to predict and prevent network failures before they occur.
- Anomaly Detection: Implement machine learning algorithms to detect unusual patterns and potential security threats.
8. Case Studies and Examples
8.1. Small Network Example (10 NEs)
Scenario: A small office network with 5 routers, 3 switches, and 2 optical transponders.
Solution: Use PRTG Network Monitor to monitor device statuses via SNMP and receive alerts through Syslog.
Steps:
- Setup PRTG: Install PRTG on a central server.
- Configure Devices: Enable SNMP and Syslog on all network devices.
- Add Devices to PRTG: Use SNMP credentials to add routers, switches, and optical transponders to PRTG.
- Create Alerts: Configure alerting thresholds for critical metrics like interface status and optical power levels.
- Monitor Dashboard: Use PRTG’s dashboard to visualize network health and receive real-time notifications of issues.
Outcome: The small network gains visibility into device performance and receives timely alerts for any disruptions, ensuring minimal downtime.
8.2. Optical Network Example
Scenario: A regional optical network with 100 optical transponders and multiple DWDM systems.
Solution: Implement OpenNMS with gNMI support for real-time telemetry and NETCONF for device configuration.
Steps:
- Deploy OpenNMS: Set up OpenNMS as the centralized network management platform.
- Enable gNMI and NETCONF: Configure all optical transponders to support gNMI and NETCONF protocols.
- Integrate OpenConfig Models: Use OpenConfig YANG models to standardize configurations across different vendors’ optical devices.
- Set Up Telemetry Streams: Configure gNMI subscriptions to stream real-time data on optical power levels and channel performance.
- Automate Configurations: Use OpenNMS’s automation capabilities to deploy and manage configurations across the optical network.
Outcome: The optical network benefits from real-time monitoring, automated configuration management, and standardized management practices, enhancing performance and reliability.
8.3. Enterprise Network Example
Scenario: A large enterprise with 10,000 network devices, including routers, switches, optical transponders, and data center equipment.
Solution: Utilize Cisco DNA Center integrated with Splunk for comprehensive management and analytics.
Steps:
- Deploy Cisco DNA Center: Set up Cisco DNA Center to manage all Cisco network devices.
- Integrate Non-Cisco Devices: Use OpenNMS to manage non-Cisco devices via NETCONF and gNMI.
- Setup Splunk: Configure Splunk to aggregate Syslog messages and telemetry data from all network devices.
- Automate Configuration Deployments: Use DNA Center’s automation features to deploy configurations and updates across thousands of devices.
- Implement Advanced Analytics: Use Splunk’s analytics capabilities to monitor network performance, detect anomalies, and generate actionable insights.
Outcome: The enterprise network achieves high levels of automation, real-time monitoring, and comprehensive analytics, ensuring optimal performance and quick resolution of issues.
9. Summary
Network Management is the cornerstone of reliable and high-performing communication networks, particularly in the realm of optical networks where precision and scalability are paramount. As networks continue to expand in size and complexity, the integration of advanced management protocols and automation tools becomes increasingly critical. By understanding and leveraging the appropriate network management protocols—such as SNMP, NETCONF, RESTCONF, gNMI, TL1, CLI, OpenConfig, and Syslog—network administrators can ensure efficient operation, rapid issue resolution, and seamless scalability.Embracing automation and standardization through tools like Ansible, Terraform, and modern network management systems (NMS) enables organizations to manage large-scale networks with minimal manual intervention, enhancing both efficiency and reliability. Additionally, adopting best practices, such as centralized management, standardized protocols, and advanced analytics, ensures that network infrastructures can meet the demands of the digital age, providing robust, secure, and high-performance connectivity.
Reference
- https://en.wikipedia.org/wiki/Software-defined_networking
- https://www.itu.int/rec/T-REC-M.3400-200002-I/en
- www.google.com