Quantum Key Distribution (QKD) for Optical Networks
Physics-Based Security for the Post-Quantum Era
Introduction: The Quantum Leap in Network Security
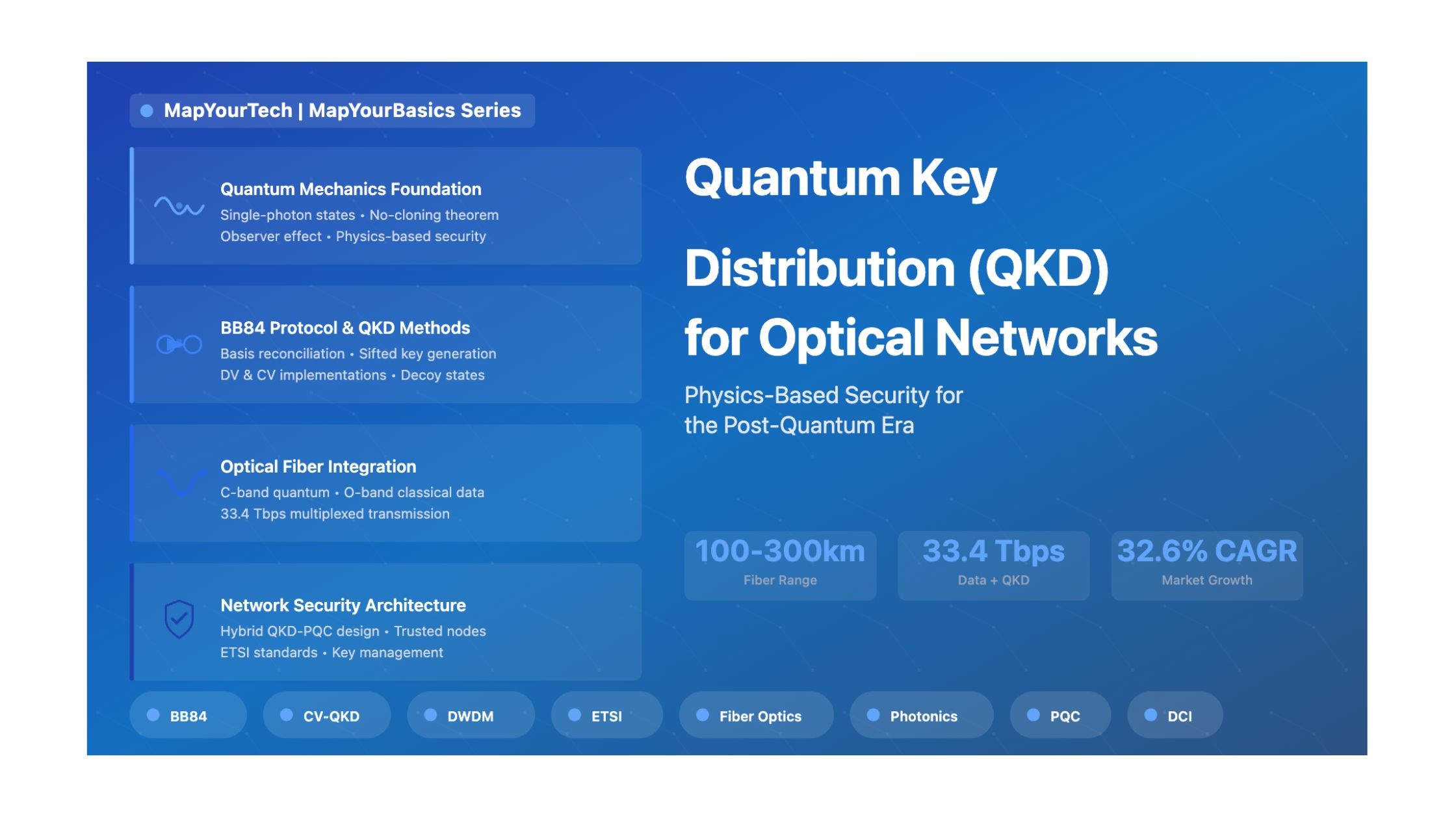
Quantum Key Distribution (QKD) represents a revolutionary approach to securing optical fiber networks, fundamentally different from traditional cryptographic methods. While conventional encryption relies on mathematical complexity, QKD leverages the immutable laws of quantum physics to guarantee secure key exchange between parties.
In today's landscape, where optical networks carry 95-99% of global internet traffic and trillions of dollars in daily financial transactions, the security imperative has never been greater. The looming threat of quantum computers capable of breaking current encryption algorithms within the 2030-2035 window has accelerated QKD deployment from research laboratories to commercial networks.
This article provides telecommunications professionals and optical network engineers with a comprehensive technical understanding of QKD technology, from fundamental quantum principles to practical implementation considerations. We'll explore how QKD integrates with existing optical infrastructure, examine real-world deployment scenarios, and outline best practices for secure network design.
Key Concepts: The Physics of Quantum Security
Fundamental Quantum Principles
QKD security derives from two cornerstone principles of quantum mechanics that make it fundamentally different from computational security:
- The Observer Effect: Measuring a quantum system inevitably disturbs it. Any attempt by an eavesdropper to observe photons carrying key information will introduce detectable anomalies in the quantum channel.
- The No-Cloning Theorem: It is physically impossible to create an identical copy of an arbitrary, unknown quantum state. This prevents attackers from intercepting and duplicating quantum key bits without detection.
How QKD Works: The BB84 Protocol
The BB84 protocol, invented by Charles Bennett and Gilles Brassard in 1984, remains the most widely implemented QKD approach. The protocol operates through a carefully choreographed quantum communication process:
- State Preparation: Alice (sender) encodes random bit values in single-photon pulses using four quantum states across two non-orthogonal bases. For polarization encoding, this typically involves rectilinear basis (|0⟩, |1⟩) and diagonal basis (|+⟩, |−⟩).
- Quantum Transmission: Single-photon pulses travel through the optical fiber quantum channel to Bob (receiver). Each photon represents one potential key bit.
- Random Measurement: Bob randomly selects one of the two measurement bases for each received photon without knowing which basis Alice used for transmission.
- Basis Reconciliation: After quantum transmission, Alice and Bob publicly announce their basis choices (but not bit values) over an authenticated classical channel. They discard measurements where basis choices didn't match.
- Key Sifting: The remaining bits where Alice and Bob used matching bases form the "sifted key." Statistically, this represents about 50% of transmitted photons.
- Error Estimation: Alice and Bob sacrifice a subset of the sifted key to estimate the Quantum Bit Error Rate (QBER). Elevated QBER indicates potential eavesdropping.
- Error Correction: Forward error correction algorithms reconcile remaining discrepancies between Alice's and Bob's keys.
- Privacy Amplification: Cryptographic hashing reduces the key length to eliminate any partial information an eavesdropper might have obtained, producing the final secure key.
Discrete Variable vs Continuous Variable QKD
Two main QKD approaches have emerged for optical networks, each with distinct technical characteristics:
| Characteristic | Discrete Variable (DV-QKD) | Continuous Variable (CV-QKD) |
|---|---|---|
| Encoding | Single-photon states in discrete bases (polarization, phase) | Optical field quadratures in continuous phase space |
| Detection | Single-photon detectors (binary outcomes) | Coherent detection with local oscillator (continuous values) |
| Protocol Example | BB84, SARG04, Decoy State | Gaussian-modulated coherent states |
| Range | 100-300 km (fiber), demonstrated to 404 km | 80-100 km (improving with technology) |
| Infrastructure | Requires specialized single-photon sources | Compatible with telecom components |
| Maturity | Most widely deployed commercially | Emerging technology, rapid development |
Secure Key Rate and Performance Metrics
The effectiveness of a QKD system is measured by several critical performance parameters:
- Sifted Key Rate: Raw bit rate after basis reconciliation, before error correction and privacy amplification.
- Secure Key Rate: Final rate of usable cryptographic keys after all processing steps. This is the metric that matters for practical applications.
- Quantum Bit Error Rate (QBER): Percentage of bits that differ between Alice and Bob after transmission. Typically must be below 11% for BB84 security proofs to hold.
- Channel Loss: Optical fiber attenuation (typically 0.2-0.25 dB/km at 1550 nm) directly impacts achievable key rate and maximum distance.
Recent demonstrations showcase impressive achievements: KDDI and Toshiba's March 2025 breakthrough achieved quantum key distribution alongside 33.4 Tbps classical data transmission over 80 km. Earlier fiber demonstrations reached 916 kbps secure key rate at 20 km, 157 kbps at 43 km, and experimental runs extending to 404 km with trusted nodes.
Practical Applications: QKD in Real-World Networks
Data Center Interconnect (DCI)
Data center interconnects represent the most commercially viable initial deployment scenario for QKD technology. The 80-100 km range limitation aligns perfectly with metropolitan DCI distances, while the high-value nature of cloud and financial data justifies the technology investment.
The March 2025 Toshiba-KDDI breakthrough directly enables DCI applications by demonstrating that quantum and classical channels can coexist on the same fiber. Secret keys are transmitted in C-band wavelengths while high-capacity data flows through O-band channels, achieving 3× capacity increase over conventional methods while maintaining quantum security.
Financial Services Networks
Major banks transmit trillions of dollars daily across optical networks, making them prime candidates for QKD deployment. Financial institutions require "defense in depth" strategies that combine multiple security layers.
- High-frequency trading: Microsecond-latency links between trading venues benefit from Layer 1 QKD encryption that adds minimal latency while ensuring transaction confidentiality.
- SWIFT messaging: International financial messaging between correspondent banks uses QKD for quantum-safe key exchange protecting sensitive transaction data.
- Securities settlement: Real-time gross settlement systems leverage QKD to secure multi-billion dollar daily settlement volumes.
Government and Defense Communications
Government agencies and military organizations were early QKD adopters due to "harvest now, decrypt later" attack concerns. Adversaries intercept encrypted communications today, storing them for decryption once quantum computers become available.
Deployment examples include quantum-secured government networks across major world capitals, military command and control communications, and classified information transmission between secure facilities. The European Space Agency's Eagle-1 satellite, launching in 2026, will provide space-based QKD as part of the EuroQCI initiative.
Metropolitan Area Networks (Q-MANs)
QKD Metropolitan Area Networks have emerged in multiple global cities, demonstrating technology maturity and multi-user network viability:
- Vienna (2008): EU-funded SECOQC network connected six computers across 200 km of fiber, supporting various CV and DV protocols.
- Shanghai (2016): First continuous-variable QKD network with four nodes connected by six fiber links ranging 2.08-19.92 km, achieving 0.25-10 kbps key rates.
- Columbus-Dublin, Ohio (2013): Battelle Memorial Institute deployed 32 km QKD link demonstrating North American commercial deployment.
Performance Benefits and ROI Considerations
Organizations evaluating QKD deployment must consider both security benefits and economic factors:
| Benefit Category | Description | Quantifiable Impact |
|---|---|---|
| Future-Proof Security | Protection against quantum computer attacks | Prevents catastrophic data breaches post-quantum era |
| Regulatory Compliance | Meeting emerging quantum-safe requirements | Avoids regulatory penalties and maintains market access |
| Infrastructure Leverage | Multiplexing with existing fiber (2025 breakthrough) | Eliminates dedicated fiber costs, ~60% CAPEX reduction |
| Competitive Advantage | Differentiation through quantum-safe offerings | Premium pricing for quantum-secured services |
| Insurance Reduction | Lower cyber insurance premiums | 15-25% premium reduction in some markets |
The QKD market is experiencing explosive growth, with forecasts projecting expansion from $480 million in 2024 to $2.63 billion by 2030 at 32.6% CAGR. This growth is driven by regulatory mandates (U.S. NSM-10, EU quantum-safe directives), technological maturity, and decreasing deployment costs due to multiplexing innovations.
Best Practices: Implementing QKD in Optical Networks
Network Architecture Design Principles
Successful QKD deployment requires careful architectural planning that accounts for quantum communication constraints:
- Distance Planning: Design network topology around the 100-300 km range limitation. For longer spans, implement trusted nodes or plan for future satellite QKD links.
- Redundancy Design: QKD links can experience downtime due to environmental factors or maintenance. Implement hybrid operation that seamlessly transitions to post-quantum cryptography when quantum keys are unavailable.
- Wavelength Management: Allocate separate wavelength bands for quantum (C-band) and classical (O-band) channels to minimize interference and maximize throughput.
- Node Security: Trusted intermediate nodes represent potential vulnerability points. Implement rigorous physical security, tamper-resistant enclosures, and continuous monitoring.
The optimal security architecture combines Quantum Key Distribution with Post-Quantum Cryptography (PQC):
- QKD for Key Exchange: Leverage physics-based security for distributing symmetric encryption keys between trusted parties.
- PQC for Authentication: Use quantum-resistant algorithms (CRYSTALS-DILITHIUM, FALCON) for digital signatures and authentication.
- Hybrid Encryption: Encrypt data with AES-256 using keys generated through both QKD and PQC key exchange for defense-in-depth.
- Graceful Degradation: Automatically fall back to PQC-only mode if QKD link fails, maintaining security without service interruption.
Common Pitfalls to Avoid
While QKD provides theoretically perfect security against quantum channel eavesdropping, practical implementations face side-channel vulnerabilities. The detector-blinding attack (2009) exploited single-photon detector characteristics to compromise systems. Modern QKD requires comprehensive security certification beyond the quantum protocol itself.
- Inadequate Error Rate Monitoring: Failing to continuously monitor QBER can miss active attacks. Implement real-time alerting for QBER threshold violations (typically >11% for BB84).
- Weak Authentication: The classical channel used for basis reconciliation must be authenticated. Compromise of this channel enables man-in-the-middle attacks despite quantum security.
- Trusted Node Vulnerabilities: Over-reliance on intermediate nodes without proper physical security creates single points of failure. Each trusted node must decrypt and re-encrypt, exposing keys momentarily.
- Insufficient Key Rate Planning: Underestimating required key consumption leads to key starvation. Account for key usage across all encrypted sessions, peak traffic periods, and error correction overhead.
- Neglecting Integration Complexity: QKD systems must integrate with existing key management infrastructure. Plan for API development, policy enforcement, and operational procedures.
Testing and Validation Approaches
Rigorous testing protocols ensure QKD system security and performance:
- Pre-Deployment Laboratory Testing: Validate quantum state preparation accuracy, single-photon source quality, detector efficiency, and QBER performance under controlled conditions.
- Fiber Characterization: Measure actual fiber attenuation, chromatic dispersion, polarization mode dispersion, and connector losses for the deployment path.
- Security Certification: Engage third-party security evaluation following ETSI QKD standards (GS QKD 008, GS QKD 014) and obtain Common Criteria certification where available.
- Interoperability Testing: Verify multi-vendor interoperability if using heterogeneous equipment. QKD standardization enables mixing vendors for transmitters, receivers, and key management systems.
- Stress Testing: Evaluate performance under adverse conditions including temperature extremes, fiber stress, adjacent channel interference, and maximum key consumption rates.
- Continuous Monitoring: Implement telemetry for secure key rate, QBER, photon detection rates, fiber attenuation, and system health metrics. Set automated alerts for anomalies.
Standards and Compliance
Multiple standards bodies have established frameworks for QKD deployment:
- ETSI (European Telecommunications Standards Institute): GS QKD series including component specifications (GR QKD 003), security requirements (GS QKD 008), and REST-based key delivery API (GS QKD 014).
- ITU-T: Study Group 13 released Y Supplement 75 specifying QKD network requirements and architectural frameworks.
- ISO/IEC: Joint Technical Committee 3 on Quantum Technologies developing international standards for quantum system evaluation and certification.
- IEEE: 802.1AE amendments adding quantum-safe options for link-layer security integration.
Optimization Strategies
Maximizing QKD system performance requires ongoing optimization:
- Decoy State Implementation: The decoy state protocol significantly improves secure key rate and transmission distance by detecting photon-number-splitting attacks. This is now standard in commercial systems.
- Adaptive Error Correction: Dynamically select error correction codes based on measured QBER rather than using fixed worst-case assumptions. This increases final key rate by 15-30%.
- Wavelength Optimization: Fine-tune quantum channel wavelength selection to minimize Raman scattering from classical channels. Proper wavelength spacing prevents noise-induced QBER elevation.
- Clock Synchronization: Maintain sub-nanosecond timing accuracy between Alice and Bob. GPS-disciplined oscillators or dedicated timing channels ensure proper photon correlation.
- Multi-User Topologies: Deploy measurement-device-independent (MDI) QKD for networks with many users. This centralizes expensive detection equipment and improves economics.
Conclusion: The Path Forward for Quantum-Safe Optical Networks
Quantum Key Distribution has evolved from a theoretical physics concept in 1984 to a commercially deployed technology securing critical infrastructure worldwide in 2025. The March 2025 breakthrough enabling 33.4 Tbps data transmission multiplexed with QKD over single fiber removes the primary economic barrier to widespread adoption, positioning QKD as a practical solution for data center interconnects, financial networks, and government communications.
- QKD provides information-theoretic security based on quantum physics, not computational hardness, making it immune to quantum computer attacks.
- The 100-300 km range limitation without trusted nodes aligns well with metropolitan network architectures and data center interconnects.
- Hybrid QKD-PQC architectures combining quantum key distribution with post-quantum cryptography provide optimal defense-in-depth.
- Recent multiplexing innovations eliminate dedicated fiber requirements, dramatically improving QKD economics.
- Standardization through ETSI, ITU-T, and ISO/IEC enables multi-vendor deployments and reduces integration risk.
Future Outlook
The QKD landscape will undergo significant transformation over the next decade:
- Satellite QKD: European Space Agency's Eagle-1 (2026) and integration with IRIS² constellation will enable global quantum networks overcoming fiber distance limitations. China's operational Micius satellite has already demonstrated intercontinental QKD.
- Quantum Repeaters: Development of quantum memory and quantum repeaters will extend range beyond current 300 km limitations without requiring trusted nodes, eliminating a key security concern.
- Integration with 5G/6G: Next-generation wireless networks will incorporate quantum-safe security from inception, with QKD securing backhaul and core network segments.
- Commercial Services: Telecommunications carriers will offer QKD-as-a-Service, making quantum security accessible to enterprises without capital investment in QKD infrastructure.
- AI-Enhanced Security: Machine learning algorithms will optimize QKD parameters in real-time, detect sophisticated attacks, and predict maintenance requirements.
Next Steps for Implementation
Organizations planning QKD deployment should:
- Conduct Security Assessment: Identify high-value data flows requiring quantum-safe protection and evaluate exposure to "harvest now, decrypt later" attacks.
- Pilot Program: Deploy QKD on a limited segment (e.g., single data center interconnect) to gain operational experience and validate integration with existing infrastructure.
- Standards Compliance: Align implementation with ETSI QKD specifications and prepare for regulatory requirements (NSM-10, EU quantum-safe directives).
- Vendor Evaluation: Assess QKD vendors based on technology maturity, standards compliance, integration capabilities, and long-term viability.
- Staff Training: Develop quantum security expertise within network operations teams through specialized training programs.
The convergence of quantum threats and quantum solutions defines the next era of optical network security. Organizations that proactively deploy QKD today will be positioned to protect their most sensitive communications against the quantum computing capabilities of tomorrow, while those who delay face the risk of catastrophic security failures when cryptographically relevant quantum computers arrive.
Developed by MapYourTech Team
For educational purposes in optical networking and telecommunications systems
Note: This guide is based on industry standards, best practices, and real-world implementation experiences from ETSI specifications, peer-reviewed research, and commercial deployments. Specific implementations may vary based on equipment vendors, network topology, and regulatory requirements. Always consult with qualified network engineers and follow vendor documentation for actual deployments. QKD security proofs assume ideal conditions; practical implementations require comprehensive security certification.
Unlock Premium Content
Join over 400K+ optical network professionals worldwide. Access premium courses, advanced engineering tools, and exclusive industry insights.
Already have an account? Log in here