HomePosts tagged “OTN”
OTN
Showing 1 - 9 of 9 results
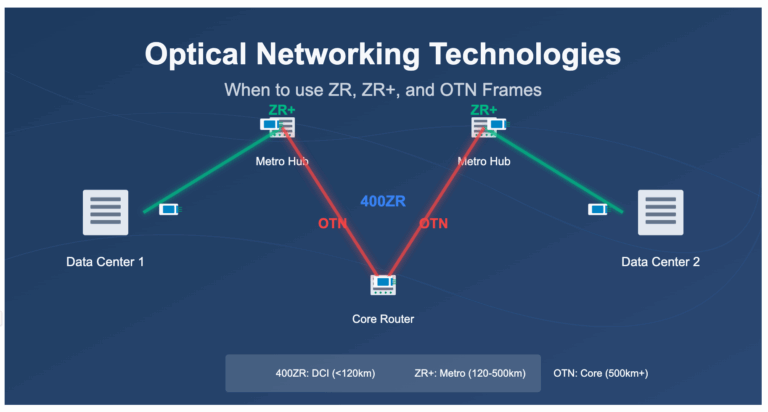
Understanding ZR, ZR+, and OTN Frames in Optical Networking Understanding ZR, ZR+, and OTN Frames in Optical Networking The evolution...
-
Free
-
April 10, 2025
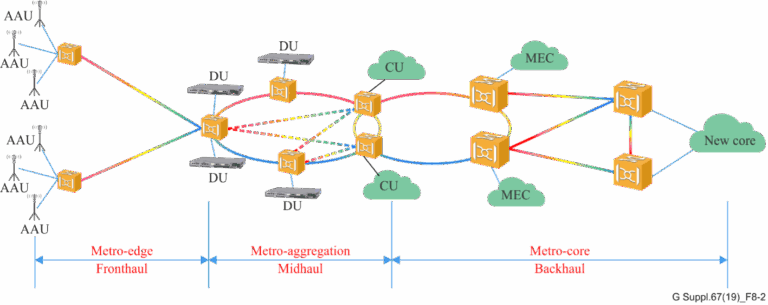
As the 5G era dawns, the need for robust transport network architectures has never been more critical. The advent of...
-
Free
-
March 26, 2025
In today’s world, where digital information rules, keeping networks secure is not just important—it’s essential for the smooth operation of...
-
Free
-
March 26, 2025
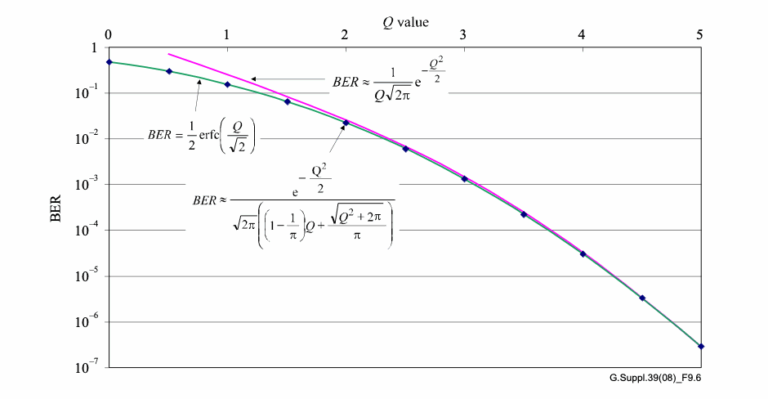
Signal integrity is the cornerstone of effective fiber optic communication. In this sphere, two metrics stand paramount: Bit Error Ratio...
-
Free
-
March 26, 2025
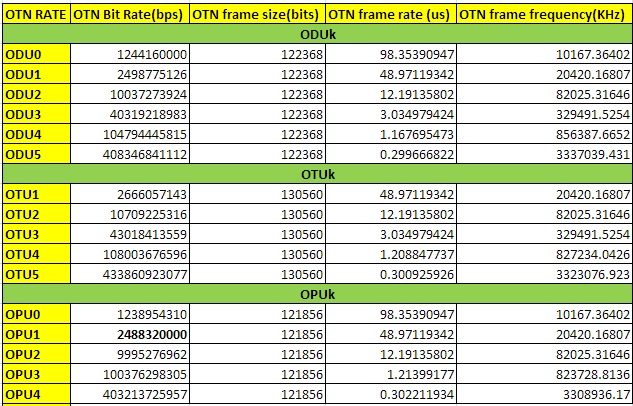
We know that in SDH frame rate is fixed i.e. 125us. But in case of OTN, it is variable rather frame size is...
-
Free
-
March 26, 2025
Here we will discuss what are the advantages of OTN(Optical Transport Network) over SDH/SONET. The OTN architecture concept was developed...
-
Free
-
March 26, 2025
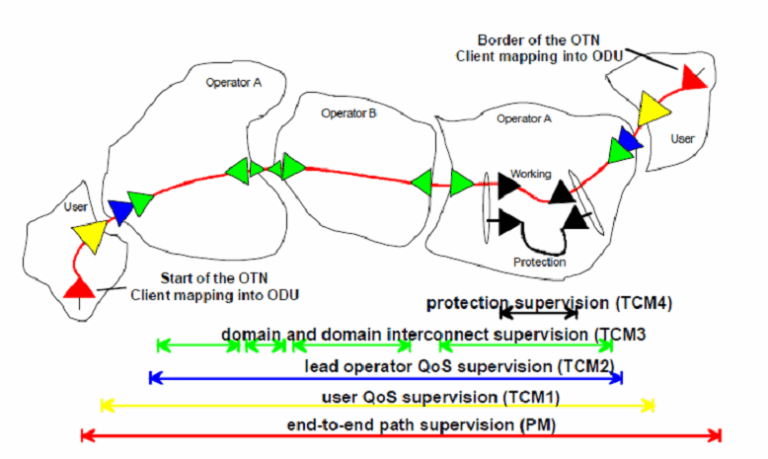
Tandem Connection Monitoring (TCM) Tandem system is also known as cascaded systems. SDH monitoring is divided into section and path...
-
Free
-
March 26, 2025
The maintenance signals defined in [ITU-T G.709] provide network connection status information in the form of payload missing indication (PMI), backward...
-
Free
-
March 26, 2025
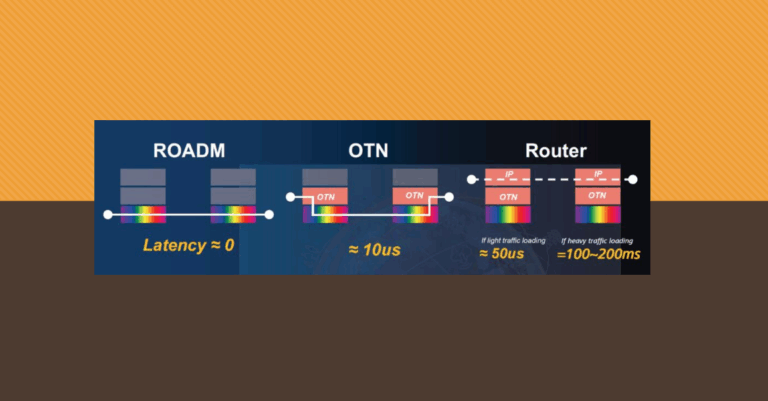
Layer 0(zero) merely introduces any latency to the network. It’s mostly the electronics that imparts latency in the network....
-
Free
-
March 26, 2025
Explore Articles
Filter Articles
ResetExplore Courses
Tags
automation
ber
Chromatic Dispersion
coherent optical transmission
Data transmission
DWDM
edfa
EDFAs
Erbium-Doped Fiber Amplifiers
fec
Fiber optics
Fiber optic technology
Forward Error Correction
Latency
modulation
network automation
network management
Network performance
noise figure
optical
optical amplifiers
optical automation
Optical communication
Optical fiber
Optical network
optical network automation
optical networking
Optical networks
Optical performance
Optical signal-to-noise ratio
Optical transport network
OSNR
OTN
Q-factor
Raman Amplifier
SDH
Signal integrity
Signal quality
Slider
submarine
submarine cable systems
submarine communication
submarine optical networking
Telecommunications
Ticker