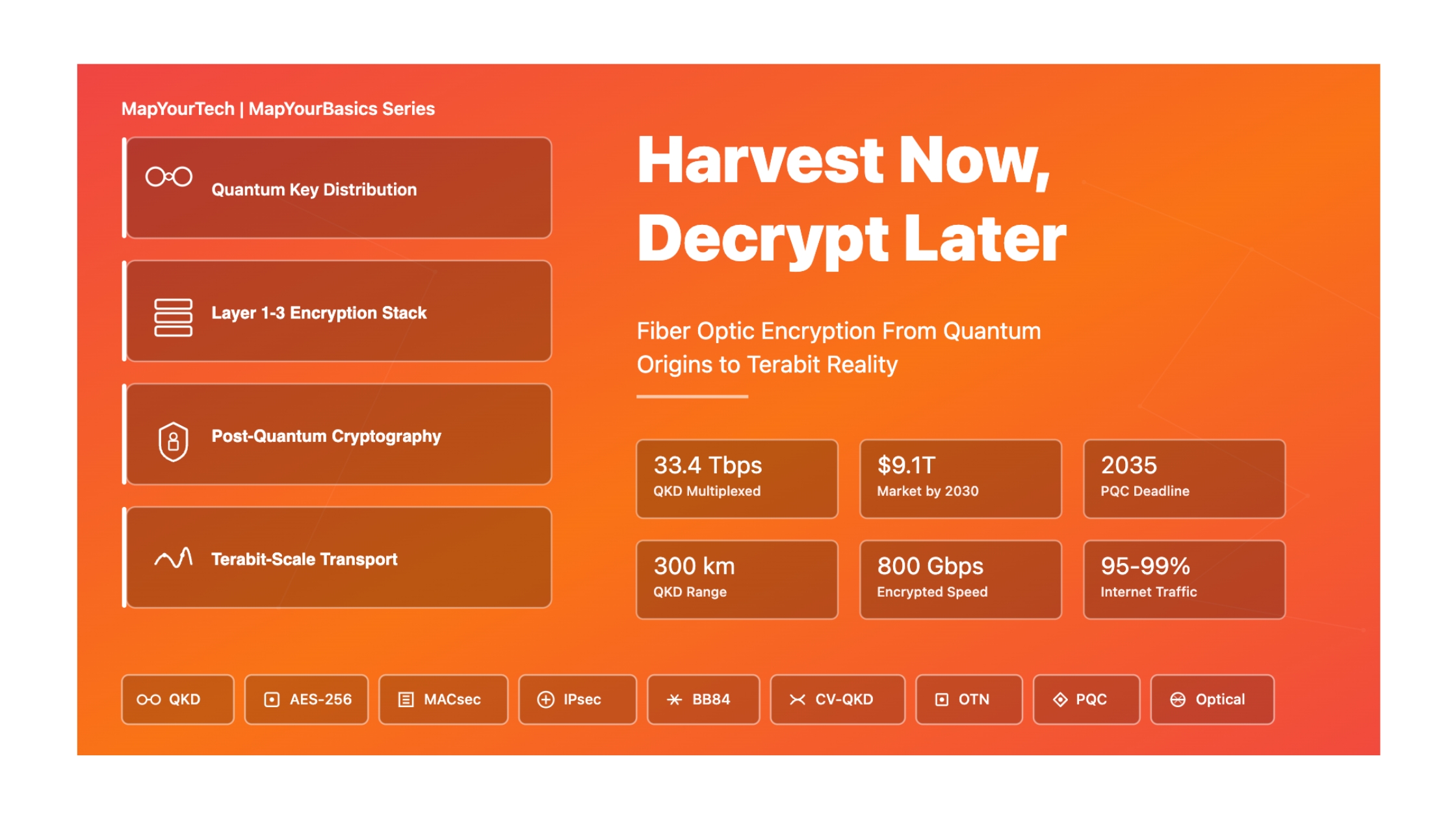
Harvest Now, Decrypt Later
Understanding the Quantum Threat to Today's Encrypted Communications and the Urgent Need for Post-Quantum Security
Fundamentals & Core Concepts
The digital world faces an unprecedented and immediate security crisis. While quantum computers capable of breaking today's encryption may still be years away, the threat is already active through a devastating attack strategy known as "Harvest Now, Decrypt Later" (HNDL).
Harvest Now, Decrypt Later (HNDL) is a cyber attack strategy where adversaries intercept and store large volumes of encrypted data today, with the expectation that they will be able to decrypt it in the future once sufficiently powerful quantum computers become available. This threat makes data that needs to remain confidential for more than a few years—such as government secrets, intellectual property, financial records, or personal health information—vulnerable right now, even though current encryption remains unbroken.
The HNDL attack exploits a fundamental asymmetry in the evolution of cryptographic technology:
- Storage is Cheap: Modern storage technology makes it economically feasible for adversaries to collect and store massive amounts of encrypted network traffic indefinitely.
- Quantum Computing Advances: Mathematician Peter Shor developed a quantum algorithm in 1994 that can efficiently solve the mathematical problems underlying RSA and Elliptic Curve Cryptography (ECC)—the foundation of most current encryption.
- Timeline Mismatch: Data collected today may remain sensitive for 10, 20, or 50+ years, while quantum computers capable of breaking current encryption are predicted to arrive within the next decade (by 2030-2035).
- Irreversible Exposure: Once data is collected, it cannot be "un-collected." If encryption is broken in the future, all historically captured data becomes retroactively compromised.
2025 (Current): HNDL attacks are already active—nation-state adversaries are harvesting encrypted communications at scale.
2028-2034: NIST predicts quantum computers capable of breaking current encryption could emerge within this timeframe.
2030-2035: Expert consensus clusters around "Q-Day"—when cryptographically relevant quantum computers (CRQC) could break RSA-2048 and ECC in practical timeframes.
2035: U.S. federal migration deadline to post-quantum cryptography under NSM-10.
The HNDL Attack Lifecycle
The attacker intercepts encrypted data today, stores it cheaply, and waits for quantum computers to decrypt it in the future.
HNDL poses an immediate threat to any organization or individual with data that requires long-term confidentiality:
- Government & Military: Classified communications, intelligence operations, defense strategies, diplomatic cables—sensitivity lasting 25-75+ years
- Healthcare: Patient medical records, genetic information, mental health data—privacy requirements for lifetime plus decades
- Financial Services: Trading algorithms, M&A negotiations, customer financial data—competitive advantage lasting 10-30 years
- Intellectual Property: R&D data, trade secrets, patent applications, pharmaceutical formulas—value persisting 10-20+ years
- Critical Infrastructure: Power grid communications, water systems, transportation networks—operational security needs spanning decades
- Personal Privacy: Biometric data, location history, communications—individual privacy concerns for lifetime
The significance of HNDL extends far beyond theoretical cryptography concerns:
- National Security: State-sponsored actors (particularly China, Russia, North Korea) are actively conducting HNDL operations against government, military, and critical infrastructure targets
- Economic Impact: The October 2024 Salt Typhoon breach—called the "worst telecom hack in U.S. history"—exposed communications from over 1 million Americans including presidential campaign staff
- Regulatory Pressure: GDPR, HIPAA, PCI-DSS requirements increasingly mandate quantum-safe protections; non-compliance risks massive penalties
- Competitive Disadvantage: Organizations slow to adopt post-quantum cryptography risk having their proprietary information compromised when competitors' protected data remains secure
- Trust Erosion: Public discovery of successful HNDL attacks could devastate consumer confidence in digital services, financial systems, and government institutions
Real-World Evidence: The threat is not hypothetical. The October 2024 Salt Typhoon incident saw Chinese state-sponsored attackers infiltrate Verizon, AT&T, Lumen Technologies, and T-Mobile networks, maintaining access for over a year. The July 2024 AT&T Snowflake breach exposed metadata from 110 million customers. These attacks demonstrate both the capability and intent of adversaries to harvest encrypted communications at massive scale.
Mathematical Framework
Understanding HNDL requires grasping the mathematical foundations that make current encryption vulnerable to quantum attacks while providing pathways to quantum-resistant alternatives.
Shor's algorithm solves the integer factorization problem exponentially faster than the best-known classical algorithms:
Compared to classical factorization:
Where:
- N = Number to be factored (RSA modulus)
- T = Time complexity
- log N = Bit length of the number
Practical Impact: A task taking a classical computer billions of years can be reduced to hours or days on a sufficiently large quantum computer.
Estimated quantum computing resources needed to break RSA encryption:
Where n = key size in bits
| Key Size | Qubits Required | Estimated Timeline | Threat Level |
|---|---|---|---|
| RSA-1024 | ~2,048 | 2028-2030 | CRITICAL |
| RSA-2048 | ~4,096 | 2030-2035 | HIGH |
| RSA-4096 | ~8,192 | 2035-2040 | MEDIUM |
Grover's algorithm provides quadratic speedup for brute-force key search:
(for n-bit key)
Effective Security Reduction:
| Algorithm | Classical Security | Quantum Security | Post-Quantum Status |
|---|---|---|---|
| AES-128 | 128 bits | 64 bits | VULNERABLE |
| AES-256 | 256 bits | 128 bits | SECURE |
Key Insight: Doubling the key size (AES-128 → AES-256) restores quantum resistance for symmetric algorithms, making AES-256 the recommended standard for post-quantum security.
Calculating the risk exposure period for encrypted data:
Where:
- T_confidentiality = Required confidentiality period (years)
- T_quantum_threat = Estimated time until quantum decryption (years from now)
Critical Decision Point: If data requires confidentiality beyond the estimated quantum threat timeline, it is already at risk and should be protected with post-quantum cryptography immediately.
Scenario: Healthcare records requiring 50-year confidentiality
Quantum Threat: Estimated 10 years until CRQC availability (2035)
Result: Data collected today will be vulnerable for 40 years (50 - 10 = 40) of its required confidentiality period, creating a massive exposure window.
The BB84 quantum key distribution protocol provides provable security based on quantum mechanics:
Where QBER = Quantum Bit Error Rate
Security Threshold: QBER must be below 11% for BB84 to remain secure against eavesdropping. Above this threshold, an adversary could have sufficient information to break the key.
Where:
- R_raw = Raw key generation rate
- h(QBER) = Binary entropy function
- Key_Rate = Secure key generation rate after error correction and privacy amplification
Visual Concepts: HNDL Attack Process
The Harvest Now, Decrypt Later Attack Lifecycle
The four-stage HNDL attack: adversaries harvest encrypted data today, store it cheaply, wait for quantum computers to become available, then decrypt historically collected communications.
Classical vs Quantum Cryptographic Vulnerability
Classical encryption (RSA, ECC) remains secure against classical computers but is vulnerable to quantum attacks. Post-quantum cryptography (ML-KEM, AES-256) resists both classical and quantum attacks.
Quantum Threat Timeline & Migration Urgency
Timeline showing HNDL threat window, quantum computing milestones, and data confidentiality requirements. Any data needing protection beyond 2030-2035 should be secured with post-quantum cryptography today.
Quantum Key Distribution vs Classical Key Exchange
Classical key exchange is vulnerable to HNDL attacks where adversaries can silently intercept and store encrypted keys. Quantum Key Distribution (QKD) makes eavesdropping detectable through quantum mechanics, preventing harvest attacks.
Attack Vectors & Adversary Capabilities
HNDL attacks are not theoretical—they are actively deployed by sophisticated adversaries with varying capabilities, motivations, and targets. Understanding these threat actors and their methods is essential for implementing appropriate defenses.
| Adversary Type | Capabilities | Primary Targets | Threat Level |
|---|---|---|---|
| Nation-State Actors (China, Russia, North Korea, Iran) |
• Direct fiber tap capabilities • Submarine cable access • Satellite interception • ISP compromise • Unlimited storage resources |
• Government communications • Military intelligence • Critical infrastructure • Defense contractors • Diplomatic channels |
CRITICAL |
| Advanced Persistent Threats (APTs) |
• Network infiltration • Man-in-the-middle attacks • ISP access via compromise • Cloud provider infiltration |
• Corporate networks • Financial institutions • Healthcare systems • Technology companies |
HIGH |
| Organized Cybercrime |
• Compromised routers/switches • Malware deployment • Traffic redirection • Limited storage capacity |
• Financial data • Payment card information • Cryptocurrency wallets • Authentication credentials |
MEDIUM |
| Insider Threats |
• Internal network access • Privileged credentials • Data exfiltration tools • Knowledge of valuable targets |
• Intellectual property • Trade secrets • Customer data • Strategic plans |
HIGH |
- Fiber Optic Tapping: Direct physical access to fiber cables using optical splitters or bend-sensitive techniques that extract light without breaking the connection. Modern taps can intercept traffic with <1 dB loss, making detection nearly impossible.
- Submarine Cable Access: Nation-states with naval capabilities can tap undersea cables at repeater sites or landing stations. Over 95% of intercontinental data travels via submarine cables.
- Internet Exchange Point (IXP) Monitoring: Major IXPs route petabytes daily. Compromising even one IXP provides access to massive international traffic flows.
- Data Center Infiltration: Physical or supply chain attacks targeting data center infrastructure where encrypted backups, replication traffic, and inter-DC communications can be harvested.
- BGP Hijacking: Malicious route announcements redirect traffic through adversary-controlled networks. The 2024 Salt Typhoon attack used persistent network access to harvest encrypted traffic from major US telecoms.
- ISP Compromise: Infiltrating Internet Service Providers provides access to aggregate customer traffic. ISPs handle unencrypted metadata even when payload is encrypted.
- DNS Manipulation: Redirecting DNS queries enables man-in-the-middle positioning for subsequent encrypted session harvesting.
- VPN Provider Compromise: Many users trust VPN providers for privacy, making them high-value targets for harvesting "protected" communications.
- TLS/SSL Downgrade: Forcing connections to use weaker ciphers or older protocol versions vulnerable to future quantum attacks.
- Certificate Authority Compromise: Stealing CA private keys enables retrospective decryption of TLS sessions if servers used non-ephemeral key exchange.
- Perfect Forward Secrecy Bypass: Many implementations don't use ephemeral keys properly. Static RSA key exchange sessions remain vulnerable to HNDL.
- Implementation Flaws: Exploiting bugs like Heartbleed to extract long-term private keys from memory, enabling historical traffic decryption.
Effective HNDL attacks require sophisticated storage infrastructure and data management capabilities:
- Storage Capacity: Modern storage costs ~$10-15 per TB. Nation-states can economically store exabytes (1,000,000 TB) of encrypted traffic.
- Bandwidth Requirements: A 100 Gbps fiber tap generates ~1 PB/day of raw traffic. Selective filtering for encrypted sessions reduces storage to manageable levels.
- Data Prioritization: Adversaries use deep packet inspection (DPI) to identify high-value targets: government TLDs, financial institutions, defense contractors, research facilities.
- Metadata Preservation: Even without decrypting payloads, storing metadata (source/destination IPs, timestamps, session lengths, protocol types) enables future correlation and analysis.
- Long-Term Archival: Tape storage and cold storage technologies provide ultra-low-cost long-term retention. LTO-9 tape: 18 TB capacity, 30-year lifespan, $100/cartridge.
Attribution: Chinese state-sponsored threat actor
Targets: Verizon, AT&T, Lumen Technologies, T-Mobile
Impact: Access to call/text metadata from 1+ million users including presidential campaign staff. Attackers maintained persistent access for over one year before detection.
Senator Mark Warner (D-VA): "Worst telecom hack in U.S. history"
HNDL Implications: Demonstrates both capability and intent of nation-state actors to conduct long-term harvesting operations against critical telecommunications infrastructure. Encrypted communications captured during this breach remain vulnerable to future quantum decryption.
Impact: Metadata exposure from 110 million customers
Data Type: Call detail records (CDRs), location data, communication patterns
HNDL Implications: Even metadata has long-term sensitivity. CDRs can reveal social networks, travel patterns, business relationships—valuable for intelligence purposes decades into the future.
NSA/CISA Joint Advisory (2024): "Nation-state adversaries are actively harvesting encrypted communications with the intent to decrypt them retroactively once quantum computing capabilities mature."
FBI Director Christopher Wray (2023): "The Chinese government is positioning itself to dominate the future quantum computing space, with implications for breaking encryption used globally."
GCHQ/NCSC Assessment (2024): Confirmed active HNDL operations targeting UK government, defense, and financial sectors by multiple nation-state actors.
Defense Strategies & Solutions
Defending against HNDL attacks requires a multi-layered approach combining immediate cryptographic upgrades, quantum-safe protocols, and architectural changes to network security. Organizations must act now—waiting until quantum computers arrive leaves years of harvested data permanently compromised.
After an 8-year evaluation process, NIST released standardized post-quantum cryptographic algorithms designed to resist both classical and quantum attacks:
| Algorithm | Type | Standard | Use Case | Status |
|---|---|---|---|---|
| ML-KEM (Module-Lattice-Based Key Encapsulation) |
Key Exchange | FIPS 203 | General-purpose encryption, TLS, VPNs | STANDARDIZED |
| ML-DSA (Module-Lattice-Based Digital Signatures) |
Digital Signature | FIPS 204 | Authentication, code signing, certificates | STANDARDIZED |
| SLH-DSA (Stateless Hash-Based Signatures) |
Digital Signature | FIPS 205 | High-security signatures, firmware | STANDARDIZED |
| FALCON | Digital Signature | FIPS 206 (Draft) | Compact signatures, constrained devices | 2025 EXPECTED |
| HQC (Hamming Quasi-Cyclic) |
Key Exchange | Selected 2025 | Alternative KEM mechanism | 2026-27 EXPECTED |
- U.S. Federal Agencies: 2035 migration deadline (NSM-10). DHS must transition by 2030.
- European Union: 2030 deadline for critical sectors (energy, telecommunications). Member states beginning migration campaigns in 2026.
- China: 2025 target for critical infrastructure PQC deployment. 2030 for state-owned enterprises.
- Private Sector: Organizations typically face 16-18 weeks to start modernization, with full transitions taking months to years.
- Estimated Costs: U.S. government non-NSS systems transition: $7.1 billion.
While PQC relies on mathematical complexity, QKD leverages the laws of physics to provide information-theoretically secure key distribution. Any eavesdropping attempt disturbs the quantum state, immediately alerting legitimate parties.
Toshiba & KDDI Research Achievement: World's first successful multiplexing of QKD with 33.4 Tbps data transmission over single optical fiber for 80 km.
- Architecture: Secret keys in C-band, high-capacity data in O-band
- Performance: 3× capacity increase over conventional 11 Tbps methods
- Impact: Eliminates dedicated dark fiber requirement, making QKD economically practical
- PQC Integration: Toshiba's systems natively incorporate NIST ML-KEM post-quantum standard for defense-in-depth
- BT & Equinix (September 2024): UK's first data center-to-data center quantum secure connection between London Canary Wharf and Slough facilities
- PacketLight & Toshiba (February 2024): QKD over DWDM validated by Japan's NICT—70-74 km long-haul links
- China (2017): Beijing-Shanghai QKD network, 2,000 km with 32 trusted relay nodes, used by major Chinese banks
- ESA Eagle-1 Satellite (2026 launch): First satellite-based QKD for EuroQCI initiative, enabling global quantum-safe communications
- Distance Limits: ~100-300 km over fiber without trusted nodes (due to photon loss)
- Key Rate: Currently 1-10 Mbps for practical systems, sufficient for symmetric key distribution but not bulk encryption
- Infrastructure Cost: Requires specialized quantum hardware, though costs decreasing with commercial adoption
- Trusted Nodes: Long-distance networks require intermediate nodes, creating potential vulnerability points
- Solution: Quantum repeaters (in development) will enable truly secure long-distance QKD without trusted intermediaries
The optimal defense against HNDL combines multiple cryptographic approaches in a defense-in-depth strategy:
Layer 1: AES-256 Symmetric Encryption
- Quantum-resistant with 128-bit effective security
- High-speed hardware acceleration available
- Protects bulk data transmission
Layer 2: Post-Quantum Key Exchange (ML-KEM)
- Establishes symmetric keys resistant to quantum attacks
- Replaces vulnerable RSA/ECC key exchange
- Software-based, deployable via firmware updates
Layer 3: Quantum Key Distribution (Optional)
- Physics-based security for highest-value communications
- Detects any eavesdropping attempts
- Provides information-theoretic security guarantee
Layer 4: Perfect Forward Secrecy
- Unique session keys for every connection
- Compromise of one session doesn't affect others
- Limits damage from HNDL attacks
- Protocol-Agnostic: Encrypts all traffic regardless of upper-layer protocols, preventing selective harvesting
- Metadata Protection: Obscures traffic patterns, connection details, and network topology—unlike IPsec/TLS which expose metadata
- Line-Rate Performance: Hardware encryption at 800 Gbps - 1.6 Tbps with <5 μs latency
- Always-On Encryption: Zero-overhead implementation means no performance penalty for enabling encryption
- Simple Key Management: Point-to-point links reduce complexity compared to network-layer solutions
Leading Implementations:
- Ciena WaveLogic 6: 1.6 Tb/s single-carrier wavelengths with AES-256-GCM, up to 6.4 Tb encrypted capacity in 2RU
- Nokia (post-Infinera acquisition): 800 Gbps-1.2 Tbps encrypted transmission, demonstrated 2,580 km reach
- PacketLight Networks: FIPS 140-2 Level 2 compliant, Common Criteria EAL2 certified Layer 1 encryption
- Risk Assessment: Identify all data with confidentiality requirements extending beyond 2030-2035
- Inventory: Catalog all cryptographic implementations and dependencies (certificates, keys, algorithms)
- Upgrade Symmetric Encryption: Migrate from AES-128 to AES-256 across all systems
- Enable Perfect Forward Secrecy: Configure all TLS implementations to use ephemeral key exchange
- Disable RSA Key Transport: Force ECDHE or DHE key exchange (temporary measure until PQC deployment)
- PQC Testing: Begin lab testing of ML-KEM implementations in non-production environments
- Vendor Assessment: Evaluate vendor roadmaps for PQC support in networking equipment, HSMs, applications
- Hybrid TLS: Deploy hybrid PQC+classical certificates where supported
- Layer 1 Encryption: For high-value links, implement optical layer encryption with AES-256
- Staff Training: Educate security and network teams on post-quantum cryptography
- Full PQC Deployment: Migrate all public-key cryptography to NIST-standardized post-quantum algorithms
- Certificate Authority Transition: Replace root and intermediate CAs with PQC-capable alternatives
- Application Updates: Ensure all applications, APIs, and services support post-quantum cryptography
- QKD Evaluation: For critical infrastructure and highest-security applications, assess QKD deployment
- Compliance Verification: Conduct third-party audits to verify quantum-safe posture
Case Studies & Practical Applications
Real-world implementations demonstrate both the threat of HNDL attacks and the effectiveness of quantum-safe countermeasures across diverse sectors.
Challenge: Major U.S. bank handling $3.9 trillion in daily transactions across 3,000+ branch locations needed to protect against HNDL attacks targeting high-frequency trading algorithms, M&A negotiations, and customer financial data with 10-30 year sensitivity.
Solution Implemented:
- Layer 1 Optical Encryption: PacketLight FIPS 140-2 Level 2 compliant encryption over DWDM links
- Performance: <5-12 μs latency for 100 GbE, meeting HFT requirements
- Architecture: Point-to-point encrypted links between trading floors, data centers, and branch networks
- Key Management: Futurex HSMs with full lifecycle management, quantum-safe key generation
Results:
- Significant reduction in attempted breaches following deployment
- Complete metadata obscurity—adversaries cannot map network topology even if intercepting traffic
- Zero performance impact on trading systems
- Regulatory compliance: PCI-DSS Requirement 4, GDPR, SOX
Lessons Learned: Layer 1 encryption essential for financial sector due to latency requirements and need for metadata protection. Future roadmap includes hybrid PQC+QKD for critical inter-DC links.
Challenge: European national healthcare network transmitting patient medical records, genetic information, and mental health data requiring lifetime+ privacy protection. Existing encryption (RSA-2048) vulnerable to HNDL with data sensitivity extending 50-75 years.
Solution Implemented:
- Post-Quantum TLS: Hybrid PQC certificates (ML-KEM + ECDHE) for web applications
- At-Rest Encryption: Migration from AES-128 to AES-256 for all stored patient records
- Network Layer: MACsec with AES-256-GCM for hospital-to-data center links
- Key Rotation: Automated hourly key rotation reducing exposure window
Results:
- Achieved quantum-safe posture ahead of GDPR quantum security recommendations
- Protected 15 million patient records from retroactive decryption
- Phased 18-month rollout across 200+ facilities
- Compliance: HIPAA encryption requirements, GDPR technical measures
Challenges: Legacy medical devices required gateway encryption appliances. Staff training on new certificate management workflows. Estimated total cost: €12 million over 3 years.
Future Plans: Evaluating QKD for connections between primary research hospitals handling cutting-edge genetic studies.
Challenge: U.S. defense contractor with classified communications requiring 75+ year confidentiality. Confirmed nation-state HNDL attempts targeting R&D data, defense strategies, and weapons system designs.
Solution Implemented:
- Defense-in-Depth Architecture:
- Layer 1: OTN encryption with AES-256 (800 Gbps wavelengths)
- Layer 2: MACsec (AES-256-XPN) for hop-by-hop security
- Layer 3: Post-quantum IPsec with ML-KEM key exchange
- QKD Deployment: 70 km QKD link between primary facility and secure backup site
- Air-Gap Networks: Highest classification data physically isolated with QKD-secured key distribution for cross-domain solutions
- Continuous Monitoring: Real-time detection of anomalous traffic patterns indicating potential interception
Results:
- Zero successful data exfiltration in 24 months post-deployment
- Detected and blocked 47 attempted network intrusions
- QKD system identified 3 fiber tapping attempts through QBER anomalies
- Compliance: NSA Suite B, FIPS 140-3, DoD cloud security requirements
Key Insight: No single technology sufficient for nation-state adversaries. Layered approach with QKD for key distribution, PQC for authentication, and Layer 1 encryption for bulk data provides comprehensive HNDL protection.
| Sector | Primary Threat | Recommended Solution | Urgency |
|---|---|---|---|
| Government/Military | Nation-state HNDL, 50-75yr confidentiality | Layer 1 + QKD + PQC triple-layer Air-gapped high-classification |
IMMEDIATE |
| Financial Services | Trading algorithms, M&A data, 10-30yr | Layer 1 optical (latency-critical) PQC for authentication |
IMMEDIATE |
| Healthcare | Patient records, genetic data, lifetime+ | PQC TLS + AES-256 at-rest MACsec for network layer |
HIGH |
| Telecommunications | Subscriber metadata, network topology | Layer 1 encryption + PQC Metadata protection essential |
HIGH |
| Energy/Utilities | SCADA, grid control, infrastructure data | Segmented networks + PQC OT-specific protocols |
HIGH |
| Technology/R&D | IP theft, trade secrets, 10-20yr value | PQC implementation + AES-256 Perfect forward secrecy |
MEDIUM-HIGH |
Note: This guide is based on industry standards, publicly available research from NIST, NSA, intelligence community assessments, and information from the project documents about quantum key distribution, post-quantum cryptography, and optical fiber encryption. Specific implementations may vary based on equipment vendors, network topology, threat models, and regulatory requirements. The timeline estimates for quantum computing capabilities represent expert consensus but involve uncertainty. Organizations should consult with qualified security professionals, conduct thorough risk assessments, and follow vendor documentation for actual deployments. This educational resource does not constitute security advice for specific systems or networks.
Unlock Premium Content
Join over 400K+ optical network professionals worldwide. Access premium courses, advanced engineering tools, and exclusive industry insights.
Already have an account? Log in here