HomePosts tagged “network automation”
network automation
Showing 1 - 10 of 10 results
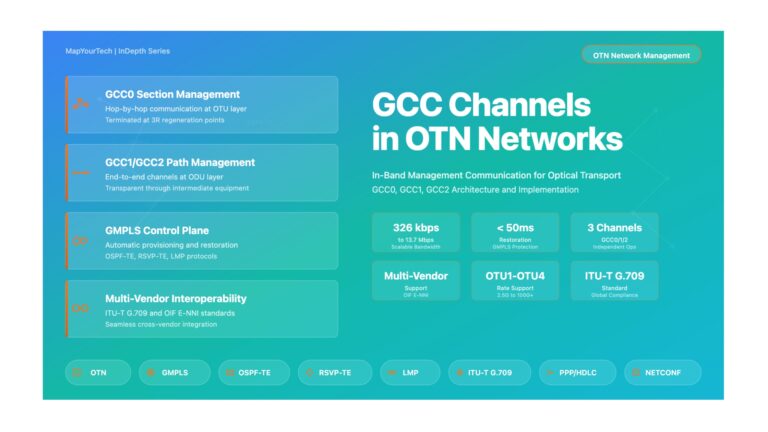
GCC Channels (GCC0/GCC1/GCC2) in OTN – Comprehensive Guide | MapYourTech GCC Channels in OTN Networks A Comprehensive Guide to General...
-
Free
-
December 30, 2025
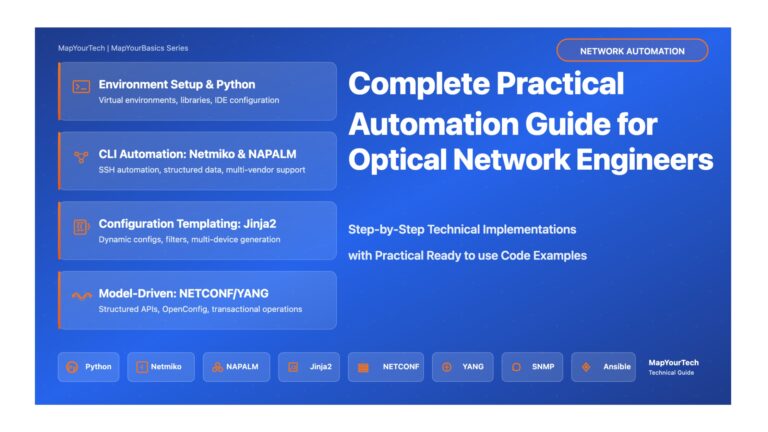
Complete Technical Guide: Automation for Optical Network Engineers Practical Automation for Optical Network Engineers Step-by-Step Implementation Guide with Real Code...
-
Free
-
November 10, 2025
Automation for Optical Networking – Part 1: Fundamentals Automation Scope for Optical Networking Professionals A Comprehensive Guide to Career Growth...
-
Free
-
November 8, 2025
TL1 (Transaction Language 1) is a command-line language used in telecommunication networks, particularly in managing optical networks. Developed in the...
-
Free
-
March 26, 2025
As modern networks scale, the demand for real-time monitoring and efficient management of network devices has grown significantly. Traditional methods...
-
Free
-
March 26, 2025
OpenConfig is an open-source, vendor-neutral initiative designed to address the growing complexity of managing modern network infrastructures. It provides standardized...
-
Free
-
March 26, 2025
Syslog is one of the most widely used protocols for logging system events, providing network and optical device administrators with...
-
Free
-
March 26, 2025
NETCONF (Network Configuration Protocol) is a modern protocol developed to address the limitations of older network management protocols like SNMP,...
-
Free
-
March 26, 2025
Simple Network Management Protocol (SNMP) is one of the most widely used protocols for managing and monitoring network devices in...
-
Free
-
March 26, 2025
Network Engineer Automation Guide | MapYourTech Network Engineer Automation Guide Master Python Programming for Modern Network Engineering Roles at AWS,...
-
Free
-
March 26, 2025
Explore Articles
Filter Articles
ResetExplore Courses
Tags
automation
ber
Chromatic Dispersion
coherent optical transmission
Data transmission
DWDM
edfa
EDFAs
Erbium-Doped Fiber Amplifiers
fec
Fiber optics
Fiber optic technology
Forward Error Correction
Latency
modulation
network automation
network management
Network performance
noise figure
optical
optical amplifiers
optical automation
Optical communication
Optical fiber
Optical network
optical network automation
optical networking
Optical networks
Optical performance
Optical signal-to-noise ratio
Optical transport network
OSNR
OTN
Q-factor
Raman Amplifier
SDH
Signal integrity
Signal quality
Slider
submarine
submarine cable systems
submarine communication
submarine optical networking
Telecommunications
Ticker