In today’s world, where digital information rules, keeping networks secure is not just important—it’s essential for the smooth operation of all our communication systems. Optical Transport Networking (OTN), which follows rules set by standards like ITU-T G.709 and ITU-T G.709.1, is leading the charge in making sure data gets where it’s going safely. This guide takes you through the essentials of OTN secure transport, highlighting how encryption and authentication are key to protecting sensitive data as it moves across networks.
The Introduction of OTN Security
Layer 1 encryption, or OTN security (OTNsec), is not just a feature—it’s a fundamental aspect that ensures the safety of data as it traverses the complex web of modern networks. Recognized as a market imperative, OTNsec provides encryption at the physical layer, thwarting various threats such as control management breaches, denial of service attacks, and unauthorized access.
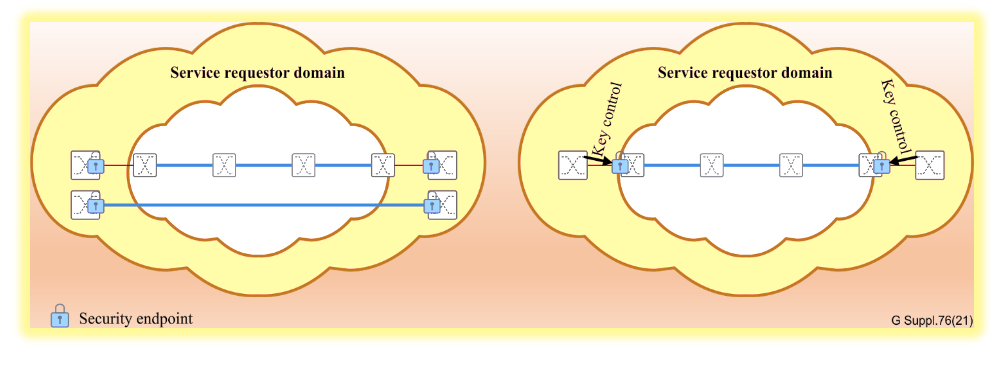
Conceptualizing Secure Transport
OTN secure transport can be visualized through two conceptual approaches. The first, and the primary focus of this guide, involves the service requestor deploying endpoints within its domain to interface with an untrusted domain. The second approach sees the service provider offering security endpoints and control over security parameters, including key management and agreement, to the service requestor.
OTN Security Applications
As network operators and service providers grapple with the need for data confidentiality and authenticity, OTN emerges as a robust solution. From client end-to-end security to service provider path end-to-end security, OTN’s applications are diverse.
Client End-to-End Security
This suite of applications ensures that the operator’s OTN network remains oblivious to the client layer security, which is managed entirely within the customer’s domain. Technologies such as MACsec [IEEE 802.1AE] for Ethernet clients provide encryption and authentication at the client level.Following are some of the scenerios.
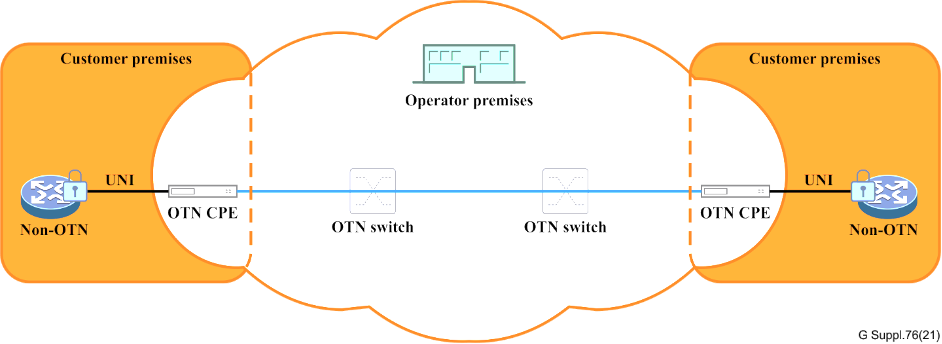
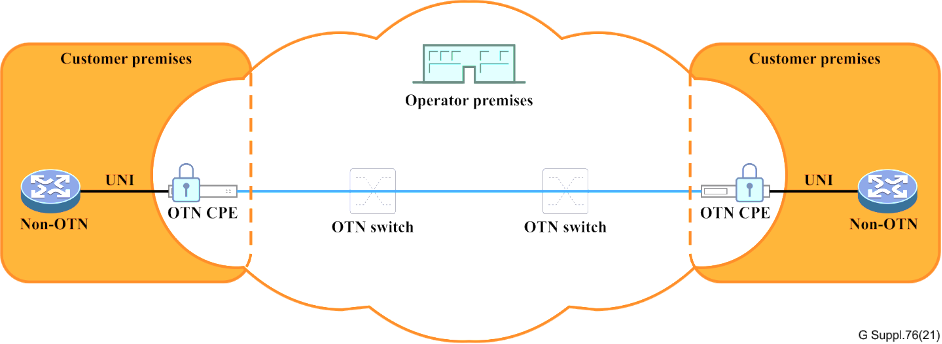
Client end-to-end security (with CPE)
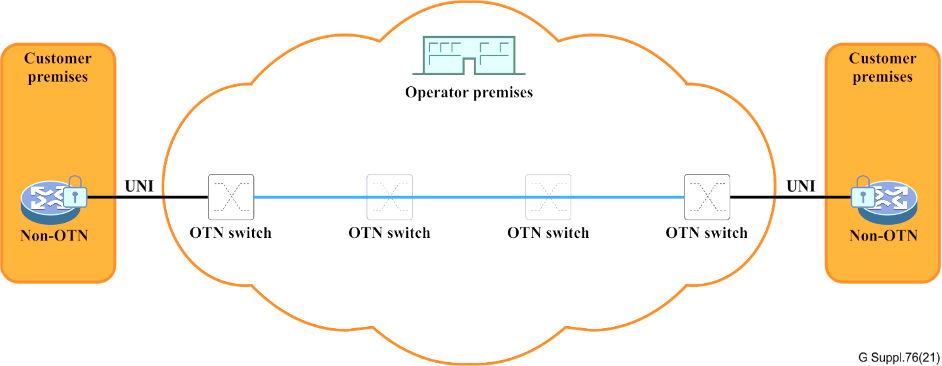
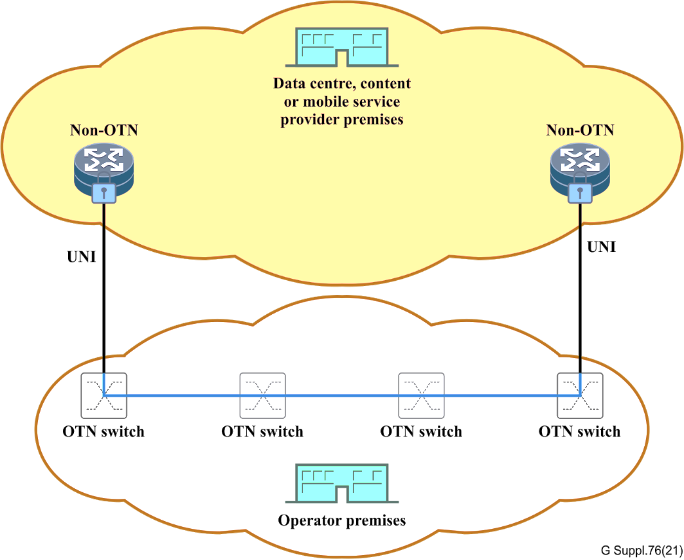
Service Provider CPE End-to-End Security
Service providers can offer security within the OTN service of the operator’s network. This scenario sees the service provider managing key agreements, with the UNI access link being the only unprotected element, albeit within the trusted customer premises.
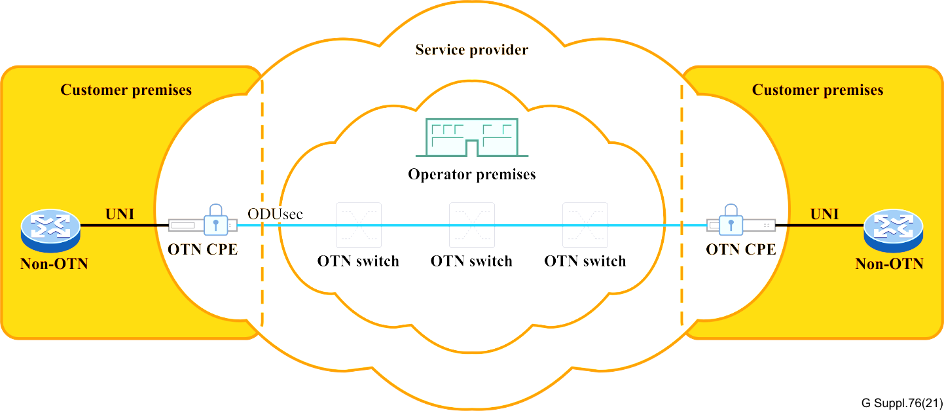
Service provider CPE end-to-end security
OTN Link/Span Security
Operators can fortify their network infrastructure using encryption and authentication on a per-span basis. This is particularly critical when the links interconnect various OTN network elements within the same administrative domain.
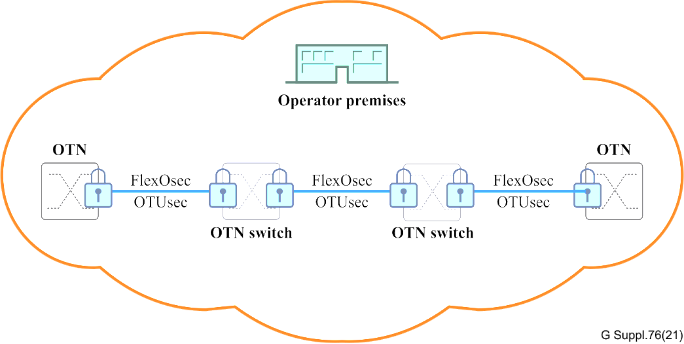
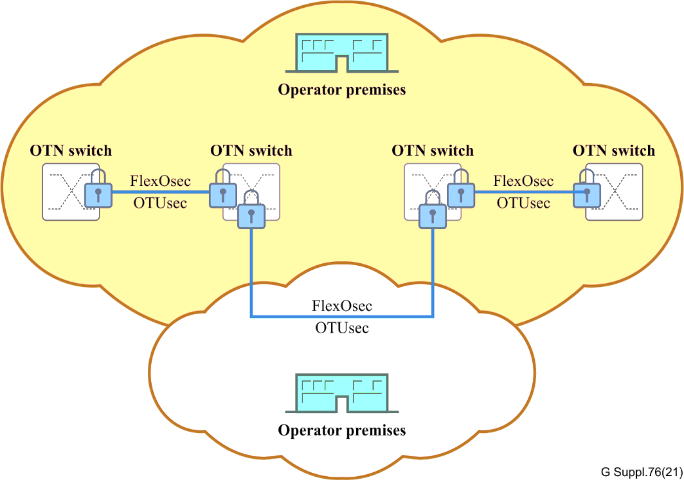
Second Operator and Access Link Security
When services traverse the networks of multiple operators, securing each link becomes paramount. Whether through client access link security or OTN service provider access link security, OTN facilitates a protected handoff between customer premises and the operator.
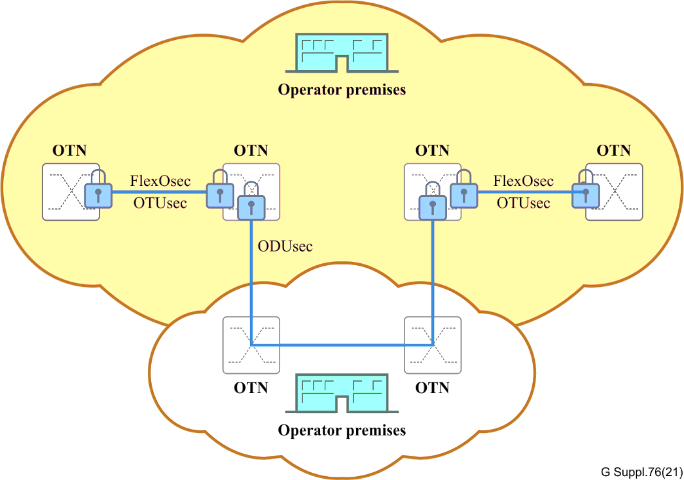
Multi-Layered Security in OTN
OTN’s versatility allows for multi-layered security, combining protocols that offer different characteristics and serve complementary functions. From end-to-end encryption at the client layer to additional encryption at the ODU layer, OTN accommodates various security needs without compromising on performance.
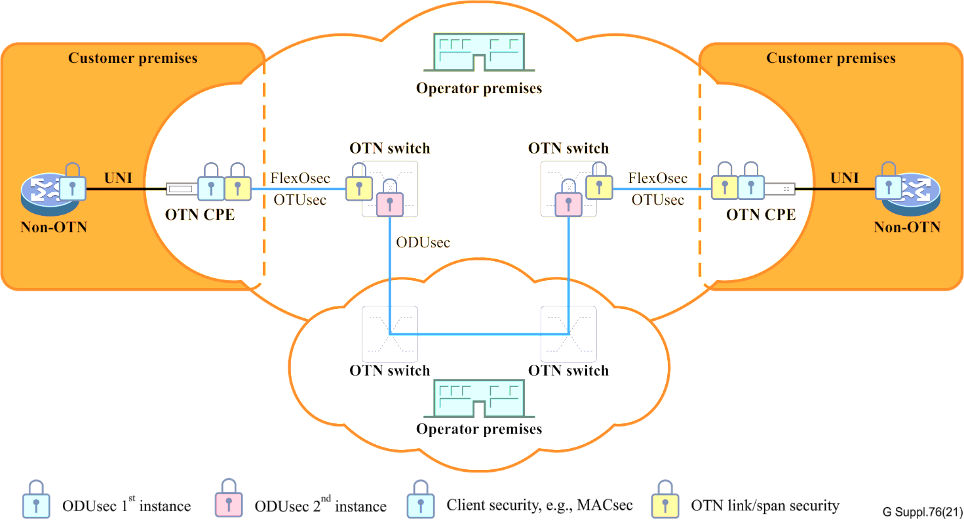
Final Observations
OTN security applications must ensure transparency across network elements not participating as security endpoints. Support for multiple levels of ODUj to ODUk schemes, interoperable cipher suite types for PHY level security, and the ability to handle subnetworks and TCMs are all integral to OTN’s security paradigm.
This blog provides a detailed exploration of OTN secure transport, encapsulating the strategic implementation of security measures in optical networks. It underscores the importance of encryption and authentication in maintaining data integrity and confidentiality, positioning OTN as a critical component in the infrastructure of secure communication networks.
By adhering to these security best practices, network operators can not only safeguard their data but also enhance the overall trust in their communication systems, paving the way for a secure and reliable digital future.
References
More Detail article can be read on ITU-T at